According to Interpol, a suspected senior member of the French-speaking hacker group OPERA1ER has been detained as part of a global law enforcement investigation known as Nervone.
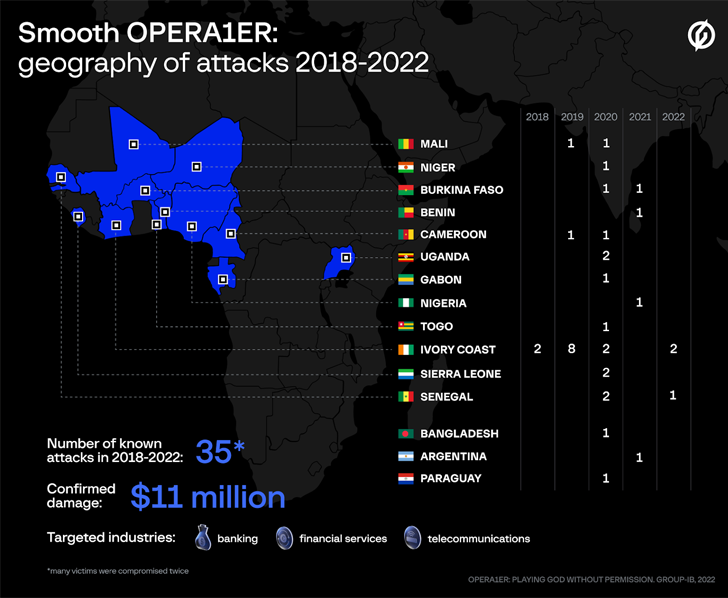
“The group is believed to have stolen an estimated USD 11 million — potentially as much as 30 million — in more than 30 attacks across 15 countries in Africa, Asia, and Latin America,” the agency stated.
Early last month, officials in Côte d’Ivoire conducted the arrest. The Criminal Investigative Division of the U.S. Secret Service and Booz Allen Hamilton DarkLabs contributed further information.
Other names for the profit-driven collective include Common Raven, DESKTOP-GROUP, and NX$M$. Group-IB and Orange CERT Coordination Centre (Orange-CERT-CC) first revealed its methods in November 2022, describing its breaches into banks, financial services providers, and telecom firms between March 2018 and October 2022.
The financial industry in Francophone nations in Africa was the focus of a series of targeted attacks from at least July 2022 to September 2022, according to Broadcom’s Symantec, which made the announcement earlier this month. According to the business, there is some overlap between the activity and OPERA1ER, which it measures as Bluebottle.
The group has used spear-phishing lures to launch attack chains that ultimately result in the use of post-exploitation tools like Cobalt Strike and Metasploit as well as commercial remote access trojans that accommodate a variety of functionalities to steal sensitive data.
Additionally, OPERA1ER has been seen repeatedly targeting the same business while keeping access to infiltrated networks for a duration of three to twelve months.
According to Group-IB, the majority of the mails were written in French and imitated phoney tax office notices or job offers. The impacted organisations’ internal payment systems were accessible to OPERA1ER, who used them to withdraw money.

