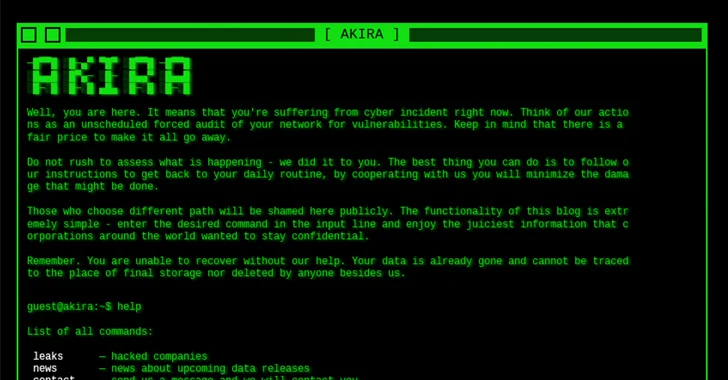
Hive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown
Two people have been detained in Australia and the United States in relation to a purported plan to create and disseminate the remote access trojan known as Hive RAT (formerly Firebird). According to the U.S. Department of Justice (DoJ), the virus “gave the malware purchasers control over victim computers and enabled them to access victims’ […]
Hive RAT Creators and $3.5M Cryptojacking Mastermind Arrested in Global Crackdown Read More »