Xenomorph Android Banking Trojan Now Spreading on Google Play Store
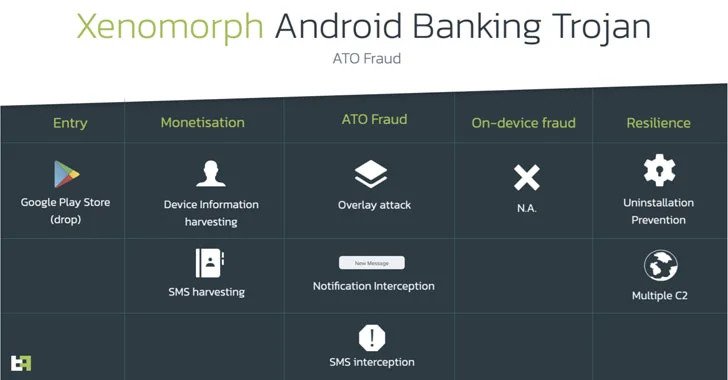
A new Android trojan has been observed to be distributed via the official Google Play Store with the goal of targeting 56 European banks and carrying out harvesting sensitive information from compromised devices. The trojan has been nicknamed Xenomorph and its noticed to share overlaps with another banking trojan tracked under the moniker Alien while […]
Xenomorph Android Banking Trojan Now Spreading on Google Play Store Read More »