It has been noted that malicious Android apps that pose as Google, Instagram, Snapchat, WhatsApp, and X (previously Twitter) can steal user credentials from devices that have been hijacked.
In a recent analysis, the threat research team at SonicWall Capture Labs stated that “this malware uses famous Android app icons to mislead users and trick victims into installing the malicious app on their devices.”
It’s unclear at this time what the campaign’s distribution vector will be. However, as soon as the users install the app on their phones, it asks for authorization to access the accessibility services and the device administrator API, which is a deprecated feature that offers system-level device administration capabilities.
By gaining access to these rights, the rogue app can take control of the device and perform arbitrary tasks, such as deploying malware and stealing data, all without the victims’ awareness.
The malware is designed to establish connections with a command-and-control (C2) server to receive commands for execution, allowing it to access contact lists, SMS messages, call logs, the list of installed apps; send SMS messages; open phishing pages on the web browser, and toggle the camera flashlight.
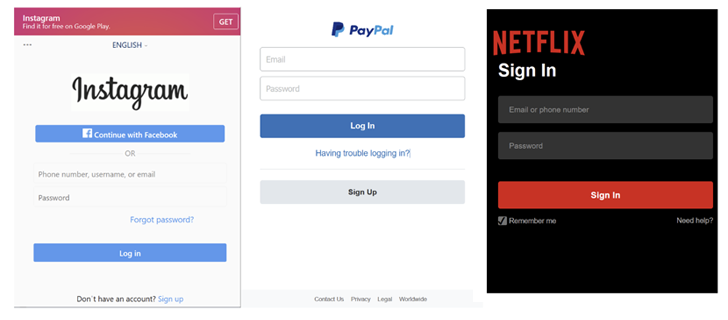
The login pages of popular services such as Facebook, GitHub, Instagram, LinkedIn, Microsoft, Netflix, PayPal, Proton Mail, Snapchat, Tumblr, X, WordPress, and Yahoo are imitated by the phishing URLs.
This discovery coincides with a warning from Cyfirma and Symantec, a division of Broadcom, about a social engineering campaign that uses WhatsApp as a delivery mechanism to spread a new piece of Android malware by pretending to be a defense-related app.
“Upon successful delivery, the application would install itself under the guise of a Contacts application,” Symantec stated. “Upon execution, the app would request permissions for SMS, Contacts, Storage, and Telephone and subsequently remove itself from view.”
It also comes after campaigns of malware distribution were found to propagate Android banking trojans such as Coper, which may display phoney window overlays and gather confidential data, tricking users into giving over their login credentials.
The National Cyber Security Centre (NCSC-FI) of Finland disclosed last week that users are being lured to Android malware that steals banking information through smishing messages.
The SMS messages encourage the receivers to call a number in relation to a debt collection claim. This approach is known as telephone-oriented attack delivery (TOAD), and it is used by the attack chain.
After the victim answers the phone, the con artist on the other end tells them that the message is fake and that they should protect themselves by installing an antivirus app on their phone.
Additionally, they tell the caller to click on a link in a follow-up text message to install what appears to be security software, but is actually malware designed to obtain login credentials for online banking accounts and eventually make illicit financial transfers.
Although NCSC-FI was unable to identify the precise strain of Android malware used in the attack, it is believed to have been Vultr, which NCC Group described earlier this month as using a nearly identical method to infect smartphones.
In recent months, malware based on Android, including Tambir and Dwphon, has also been found in the wild with different device gathering capabilities. Dwphon is primarily targeted at the Russian market and targets mobile phones manufactured by Chinese manufacturers.
“Dwphon comes as a component of the system update application and exhibits many characteristics of pre-installed Android malware,” Kaspersky stated.
“The exact infection path is unclear, but there is an assumption that the infected application was incorporated into the firmware as a result of a possible supply chain attack.”
According to telemetry data examined by the Russian cybersecurity company, the number of Android users targeted by banking malware surged from 57,219 to 75,521 in the previous year, a 32% rise. The countries of Turkey, Saudi Arabia, Spain, Switzerland, and India have recorded the most infections.
“Although the number of users affected by PC banking malware continues to decline, […] the year 2023 saw the number of users encountering mobile banking Trojans increase significantly,” Kaspersky stated.
Follow us for more interesting news like this on X Instagram

