An ongoing effort of cryptojacking has been brought to light by cybersecurity researchers, which mines Dero money using misconfigured Kubernetes systems.
The activity was made public by cloud security company Wiz, which stated it was an enhanced version of a financially driven operation that CrowdStrike had initially reported on in March 2023.
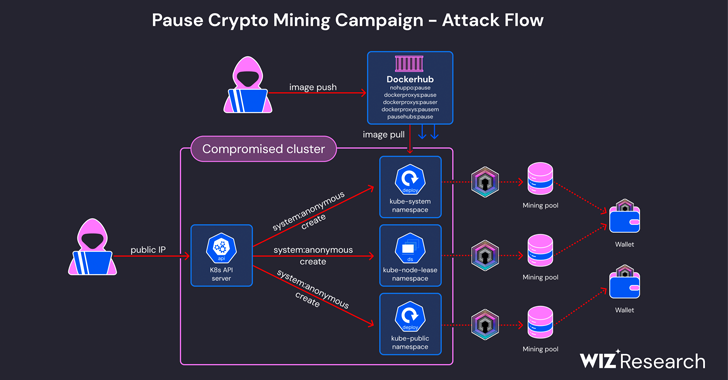
Wiz researchers Avigayil Mechtinger, Shay Berkovich, and Gili Tikochinski stated, “In this incident, the threat actor abused anonymous access to an Internet-facing cluster to launch malicious container images hosted at Docker Hub, some of which have more than 10,000 pulls.” “These docker images contain a UPX-packed DERO miner named ‘pause.'”
The first step in gaining access is to send the miner payloads to externally reachable Kubernetes API servers that have allowed anonymous authentication.
In contrast to the 2023 version, which used the Kubernetes DaemonSet “proxy-api,” the most recent flavour uses the DaemonSets “k8s-device-plugin” and “pytorch-container,” which appear to be innocuous, to run the miner on every cluster node.
Furthermore, the “pause” container’s name is an attempt to mimic the real “pause” container, which is used to ensure network isolation and bootstrap pods.
The wallet address and unique URLs for each Dero mining pool are hardcoded into the open-source, Go-written bitcoin miner. Additionally, it is obfuscated to thwart examination using the freely available UPX packer.
The primary benefit of encoding the mining setup into the code is that it allows the miner to be operated without the need for any command-line parameters, which are usually inspected by security measures.
Wiz claimed to have discovered other tools created by the threat actor, including as a Windows sample of a Dero miner loaded with UPX and a dropper shell script intended to remove GMiner from GitHub and end rival miner operations on an affected computer.
“[The attacker] registered domains with innocent-looking names to avoid raising suspicion and to better blend in with legitimate web traffic, while masking communication with otherwise well-known mining pools,” stated the investigators.
“These combined tactics demonstrate the attacker’s ongoing efforts to adapt their methods and stay one step ahead of defenders.”