An extensive series of credential phishing campaigns has been discovered and disclosed by Microsoft on Thursday. This campaign is taking advantage of custom phishing kit that stitched together components from at least five different circulated ones with the aim of siphoning user login information.
This discovery was first made in December 2020 and dubbed the copy-and-paste attack infrastructure “TodayZoo”.
Researchers have stated that “availability of numerous phishing kits for sale and for rent makes it easy for a lone wolf attacker to pick and choose the best features from these kits, they put these functionalities together in a customized kit and try to reap the benefits all to themselves. Such is the case of TodayZoo.”
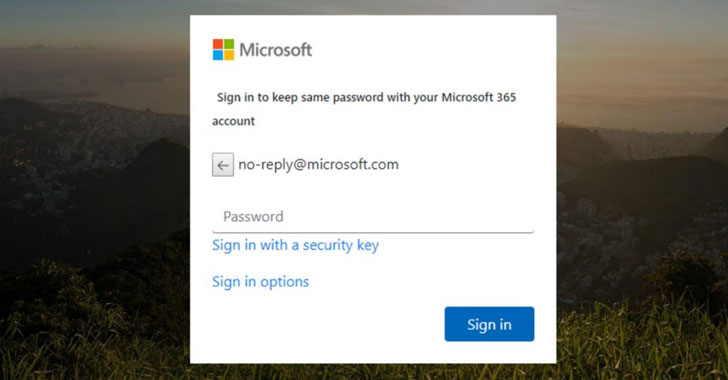
The TodayZoo phishing campaign impersonates Microsoft, posing as a password reset or fax and scanner notifications, to redirect victims to credential harvesting pages.
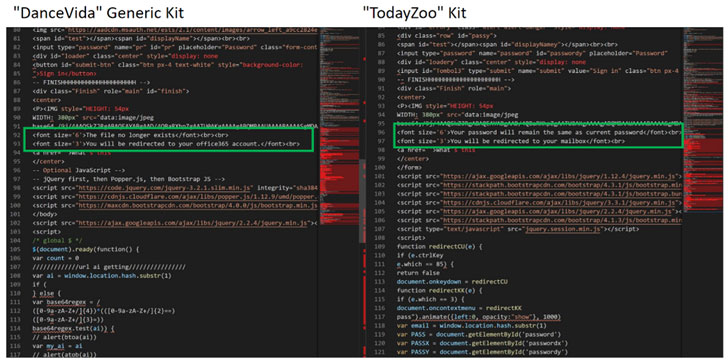
Large part of TodayZoo is believed to have been lifted generously from another kit known as DanceVida, while imitation and obfuscation-related components significantly overlap with the code from at least four other phishing kits such as Botssoft, WikiRed, Office-RD117 and Zenfo.
“This research further proves that most phishing kits observed or available today are based on a smaller cluster of larger kit ‘families,'” Microsoft’s analysis read. “While this trend has been observed previously, it continues to be the norm, given how phishing kits we’ve seen share large amounts of code among themselves.”
TodayZoo however deviates from DanceVida with regards to the credential harvesting component by replacing the original functionality with its own exfiltration logic.