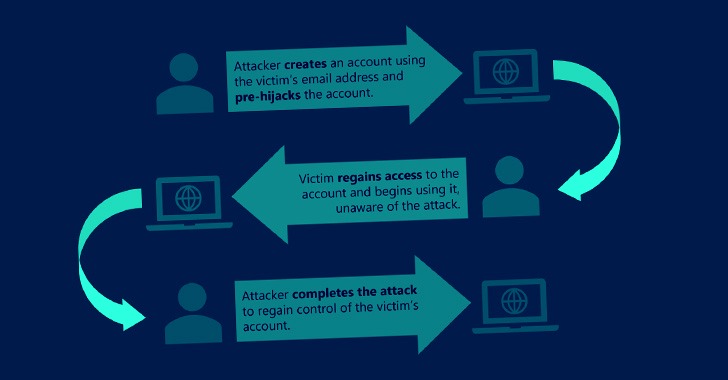
According to new research, malicious actors can get illegal access to users’ online accounts via a new approach known as “account pre-hijacking.”
The assault targets the account creation process, which is common on websites and other online platforms, allowing an adversary to carry out a series of operations before an unwary victim establishes an account with a target service.
Avinash Sudhodanan, an independent security researcher, led the investigation with Andrew Paverd of the Microsoft Security Response Center (MSRC).
Pre-hijacking relies on an attacker already having a unique identifier linked with a victim, such as an email address or phone number, which can be obtained through scraping the target’s social media accounts or credential dumps circulating on the internet as a result of numerous data breaches.
The attacks can then take five different forms, including both the adversary and the victim using the same email address when creating the account, potentially providing both sides concurrent access to the account.
Pre-hijacking attacks have the same effect as account hijacking in that they allow the adversary to gain unauthorized access to the victim’s personal information or even impersonate the victim, depending on the nature of the service.
“If an attacker can create an account at a target service using the victim’s email address before the victim opens an account, the attacker can use various approaches to place the account in a pre-hijacked state,” the researchers wrote.
“After the victim regained access to the account and began using it, the attacker may regain access and take control the account.” The following are the five types of pre-hijacking attacks:
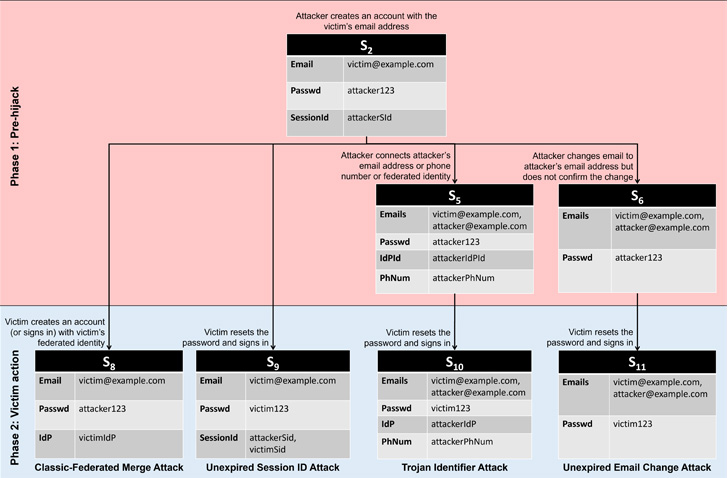
Classic-Federated Merge Attack- allows the victim and the attacker to access the same account by merging two accounts created using classic and federated identity routes with the same email address.
Unexpired Session Identifier Attack- in which the attacker establishes an account with the victim’s email address and keeps it active for a long time. Because the password reset did not end the attacker’s session, when the user restores the account using the same email address, the attacker retains access.
Trojan Identifier Attack- in which an attacker creates an account using the victim’s email address and then adds a trojan identifier, such as a secondary email address or a phone number under their control, to the account. When the actual user regains access to the account after a password reset, the attacker can utilize the trojan identifier to gain access.
Unexpired Email Change Attack- An attacker opens an account with the victim’s email address and then changes the email address to one they control. When the service provides the new email address a verification URL, the attacker waits for the victim to recover and start using the account before completing the change-of-email process and seizing control of the account.
Non-Verifying Identity Provider (IdP) Attack- using a non-verifying IdP, the attacker creates an account with the target service. If the victim uses the traditional registration method and uses the same email address, the attacker can acquire access to the account.
In an Alexa examination of 75 of the most popular websites, 56 pre-hijacking vulnerabilities on 35 services were discovered. There are 13 Classic-Federated Merge attacks, 19 Unexpired Session Identifier attacks, 12 Trojan Identifier attacks, 11 Unexpired Email Change attacks, and one Non-Verifying IdP attack across various platforms. –
- Dropbox – Unexpired Email Change Attack
- Instagram – Trojan Identifier Attack
- LinkedIn – Unexpired Session and Trojan Identifier Attacks
- WordPress.com – Unexpired Session and Unexpired Email Change Attacks, and
- Zoom – Classic-Federated Merge and Non-verifying IdP Attacks
While strict identification verification in services is critical for preventing pre-hijacking attacks, users should employ multi-factor authentication to protect their accounts (MFA).
“Correctly designed MFA will prohibit the attacker from authenticating to a pre-hacked account after the victim begins using it,” the researchers wrote. “To prevent the Unexpired Session attack, the service must additionally invalidate any sessions formed previous to the activation of MFA.”
In addition, for a defense-in-depth approach to account management, online services should remove unverified accounts on a regular basis, enforce a short timeframe to authenticate a change of email address, and invalidate sessions during password resets.
Watch Cybernews broadcast and many more ethical hacking tutorials on our channel:
Follow us on YouTube to learn Ethical Hacking and how to keep safe in the cyberworld.