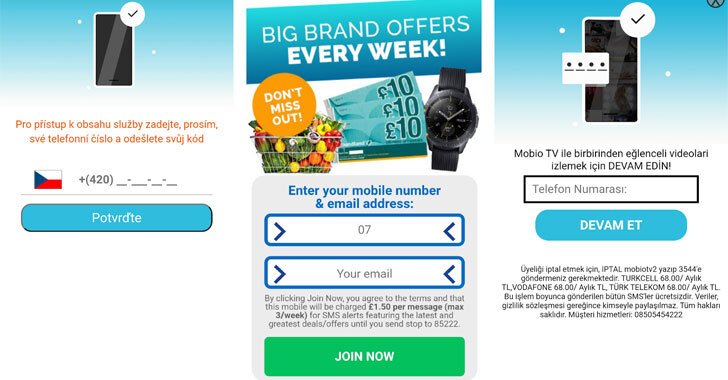
Chinese Payment-Terminal Company Raided By The FBI
In furtherance of a federal investigation the FBI has searched the Florida premises of a Chinese payment-terminal provider. This comprised of the warehouse and offices belonging to Pax Technology. Pax was founded two decades ago and is headquartered in Shenzhen. According to its website, the company has delivered over 57 million terminals to more than […]
Chinese Payment-Terminal Company Raided By The FBI Read More »