The evolution of Jupyter, a .NET infostealer has been reported by Cybersecurity researchers. This is known for going at healthcare and education sectors, making it exceptional at defeating most endpoint security scanning solutions.
Morphisec underscores that the malware has not just continued to remain active but also showcases “how threat actors continue to develop their attacks to become more efficient and evasive.” The Isreali company said it’s currently investigating the sale and scope of the attacks.
Jupyter (aka Solarmarker) was documented in November 2020 and was said to be likely of Russian origin and primarily targets Chromium, Firefox and Chrome browser data, with additional capabilities that allow for full backdoor functionality, including features to siphon information and upload the details to a remote server and download and execute further payloads. Multiple versions of Jupyter began emerging in May 2020 this is based on forensic evidence gathered by Morphisec.
In August 2021, Cisco Talos attributed the intrusions to a “fairly sophisticated actor largely focused on credential and residual information theft.” Cybersecurity firm CrowdStrike, earlier this February, described the malware as packing a multi-stage, heavily obfuscated PowerShell loader, which leads to the execution of a .NET compiled backdoor.
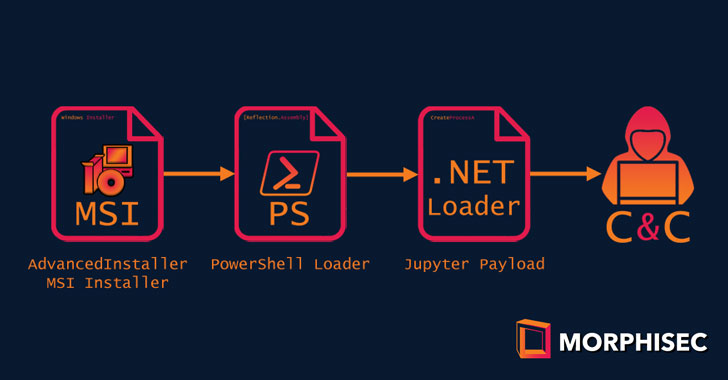
Previous attacks had incorporated legitimate binaries of well-known software such as Docx2Rtf and Expert PDF, however the latest delivery chain puts to use another PDF application called Nitro Pro. Starting with a deployment of an MSI installer payload that’s over 100MB in size, allowing them to bypass anti-malware engines and obfuscated using a third-party application packaging wizard called Advanced Installer.
See also: How to create a payload to infect a windows machine with Metasploit.
Running the MSI payload leads to the execution of a PowerShell loader embedded within a legitimate binary of Nitro Pro 13, two variants of which have been observed signed with a valid certificate belonging to an actual business in Poland, suggesting a possible certificate impersonation or theft. The loader, in the final-stage, decodes and runs the in-memory Jupyter .NET module.
“The evolution of the Jupyter infostealer/backdoor from when we first identified it in 2020 proves the truth of the statement that threat actors are always innovating,” Morphisec researcher Nadav Lorber said. “That this attack continues to have low or no detections on VirusTotal further indicates the facility with which threat actors evade detection-based solutions.”