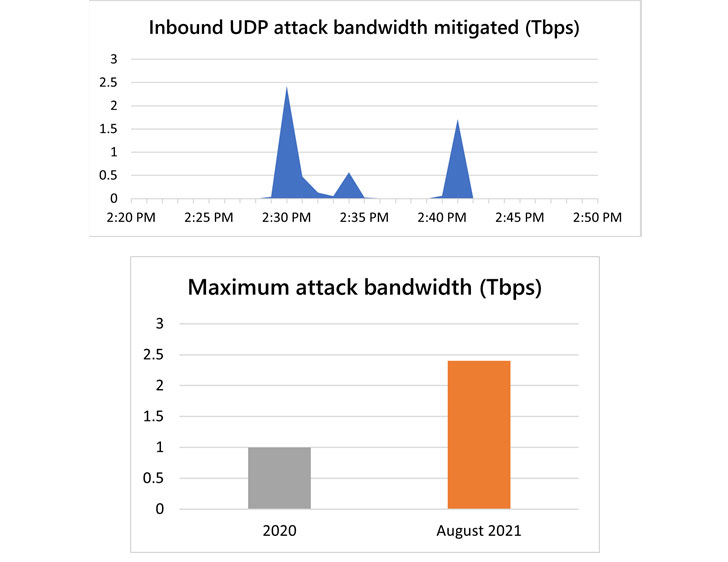
Microsofts Azure cloud platform suffered a 2.4 Tbps distributed denial-of-service (DD0S) attack in the last week of August however this was mitigated. The attack targeted an unnamed customer in Europe surpassing a 2.3 Tbps attack stopped by Amazon Web Services in February 2020.
Amir Dahan, senior program manager of Azure Network has said in a post that the it was a “140% higher attack than the 2020’s 1 Tbps attack and higher than any network volumetric even previously detected on Azure calling it a UDP reflection lasting for about 10 minutes.
Reflected amplification attacks are a type of denial of service attacks wherein a threat actor takes advantage of the connectionless nature of UDP protocol with spoofed requests so as to overwhelm a target server or network with a flood of packets, causing disruption or rendering the server and its surrounding infrastructure unavailable.
A reflection attack involves an attacker spoofing a target’s IP address and sending a request for information, primarily using the User Datagram Protocol (UDP) or in some caes, the Transmission Control Protocol (TCP). The server then responds to the request, sending an answer to the target’s IP address. This “reflection”—using the same protocol in both directions—is why this is called a reflection attack.. Any server operating UDP or TCP-based services can be targeted as a reflector.
The origin of the attack can be traced back to approximately 70,000 compromised devices primarily located in Japan, Taiwan, Malaysia, Vietnam, China and USA.
This news is coming months after Russian internet giant Yandex became the target of a record-breaking distributed denial-of-service( (DDoS) attack by a new botnet called Mēris, battering the companies web infrastructure with millions of HTTP requests, before hitting a peak of 21.8 million requests per second (RPS).