Cybersecurity researchers have on Tuesday discovered a mass volume of email attack notably targeting Germany and Australia. This campaign has beeen tied to the TA505 which is the name assigned to the financially motivated threat group that’s been in active cybercrime business since at least 2014 and is behind the infamous Dridex anking trojan as well as the Locky ransomware.
Cybersecurity company Morphisec Labs is tracking the same attack chain under the independent moniker “MirrorBlast.”
The attacks originated as a a series of low-volume email waves, sending only several thousand messages in each stage before increasing in late September and as recently as October 13, resulting in tens of thousands of emails.
The campaigns have been observed to strongly resemble the historic TA505 activity from 2019 and 2020. The commonalities include similar domain naming conventions, email lures and delivery of the FlawedGrace remote access trojen (RAT).
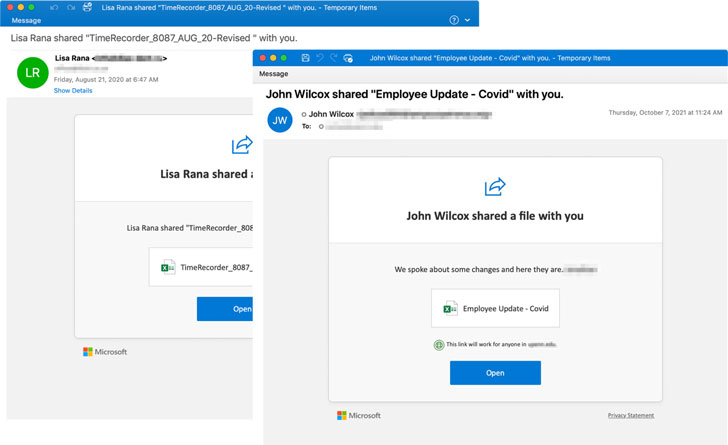
The group is known to strike research institutes, banks, energy companies and government agencies for profit-seeking motives with the malicious activity typically commencing upon opening malware-laced attachments in phishing messages purported to be related to COVID-19 updates, insurance claims or notifications about Microsoft OneDrive shared files.
NCC group have stated that throughout the years the group heavily relied on third party services and tooling to support its fraudulent activities, however, the group now mostly operates independently from initial infection until monetization.
FlawedGrace is a fully featured remote access trojan (RAT) written in C++ and deliberately designed to thwart reverse-engineering and analysis. It possesses the capability to establish communications with a command-and-control server to receive instructions and exfiltrate the results of those commands back to the server.