A Zero-day vulnerability has been disclosed in Palo Alto Networks GlobalProtect VPN capable of being abused by an unauthenticated network-based attacker to execute arbitrary code on affected devices using root privileges
Tracked as CVE-2021-3064 (CVSS score:9.8), the security weakness impacts PAN-OS 8.1 versions earlier than PAN-OS 8.1.1.17.
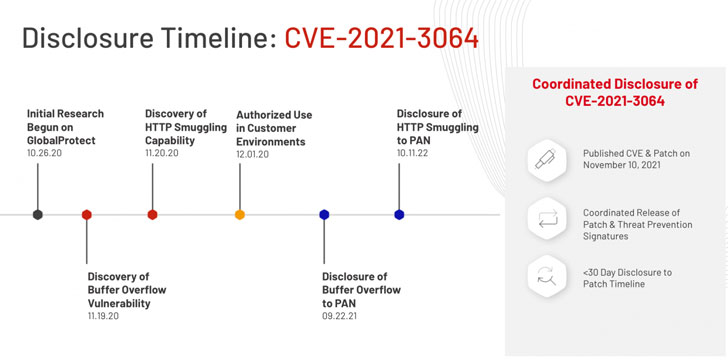
This flaw was discovered and reported by Masachusetts-based cybersecurity firm Randori and is tracked as CVE-2021-3064 (CVSS score: 9.8). It has also been indicated that the security weakness impacts PAN-OS 8.1 versions earlier than PAN-OS 8.1.17.
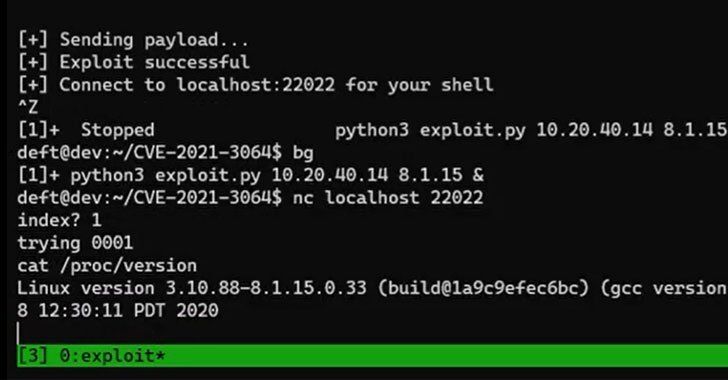
Randori researchers have stated that the vulnerability chain consists of a method for bypassing validations made by an external web server (HTTP smuggling) and a stack-based buffer overflow. The Exploitation of the vulnerability chain has been proven and allows for remote code execution on both physical and virtual firewall products.
The technical details related to CVE-2021-3064 is currently being witheld for 30 days in order to prevent threat actors from abusing the vulnerability to stage real-world attacks.
The security bug stems from a buffer overflow that occurs while parsing user-supplied input. Successful exploitation of the flaw necessitates that the attacker strings it with a technique known as HTTP smuggling to achieve remote code execution on the VPN installations, not to mention have network access to the device on the GlobalProtect service default port 443.
Premised on the fact that VPN devices are lucrative targets for malicious actors, it is recommended that users patch the vulnerability. Palo Alto Networks is advising affected organizations to enable threat signatures for identifiers 91820 and 91855 on traffic destined for GlobalProtect portal and gateway interfaces to prevent any potential attacks against CVE-2021-3064.