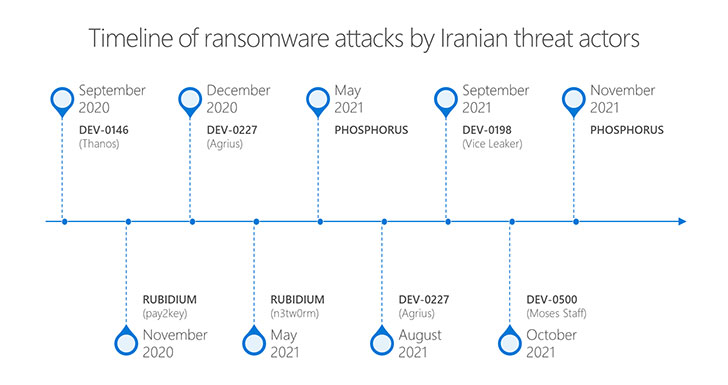
There has been an increase in the adoption of ransomware as a means of generating revenue for nation-state operators with affiliations with Iran. So far, six threat actors with the West Asian country have been discovered deploying ransomware to achieve their strategic objectives, researchers from Microsoft Threat Intelligence Center (MSTIC) revealed, adding that the ransomware deployments were launched in waves every six to eight weeks on average.
Of note is a threat actor tracked as Phosphorus (aka Charming Kitten or APT35), which has been found scanning IP addresses on the internet for unpatched Fortinet FortiOS SSL VPN and on-premises Exchange Servers to gain initial access and persistence on vulnerable networks, before moving to deploy additional payloads that enable the actors to pivot to other machines and deploy ransomware.
Other tactics used to enable faster spread was to create a few fictitious social media accounts including one of attractive ladies to build trust and after a few months deliver malware-laced documents that allow for data exfiltration from the victims systems. This tactics has been adopted by Phosphorus and another threat actor dubbed Curium.
“The attackers build a relationship with target users over time by having constant and continuous communications which allows them to build trust and confidence with the target,” MSTIC researchers said. In many of the cases we have observed, the targets genuinely believed that they were making a human connection and not interacting with a threat actor operating from Iran.”
Also there was a use of password spray attack targeting Office 365 tenants targeting U.S., E.U., and Isreali defense technology companies.
The findings are especially significant in light of a new alert issued by cybersecurity agencies from Australia, the U.K., and U.S., warning of an ongoing wave of intrusions carried out by Iranian government-sponsored hacking groups by exploiting Microsoft Exchange ProxyShell and Fortinet vulnerabilities.
“These Iranian government-sponsored APT actors can leverage this access for follow-on operations, such as data exfiltration or encryption, ransomware, and extortion,” the agencies said in a joint bulletin published Wednesday.