The dark web payment portal operated by Conti the ransomware group has gone down in what appears to be a shift to a new infrastructure after details of inner working of the group was made public.
According to MalwareHunterTeam, “while both the clearweb and Tor domains of the leak site of the Conti ransomware gang is online and working, both their clearweb and Tor domains for the payment site (which is obviously more important than the leak) is down.”
It’s not clear what prompted the shutdown, but the development comes as Swiss cybersecurity firm PRODAFT offered an unprecedented look into the group’s ransomware-as-a-service (RaaS) model, wherein the developers sell or lease their ransomware technology to affiliates hired from darknet forums, who then carry out attacks on their behalf while also netting about 70% of each ransom payment extorted from the victims.
This has resulted in the identification of 3 members of the Conti team each playing administrative roles (“Tokyo”), assistant (“it_work_support@xmpp[.]jp”), and recruiter (“IT_Work”) to attract new affiliates into their network.
While ransomware attacks work by encrypting the victims’ sensitive information and rendering it inaccessible, threat actors have increasingly latched on to a two-pronged strategy called double extortion wherein they demand ransom payment for decrypting data and also threatening to publish the stolen information if payment is not received within a specific deadline.
“Conti customers – affiliate threat actors – use [a digital] management panel to create new ransomware samples, manage their victims, and collect data on their attacks,” noted the researchers, detailing the syndicate’s attack kill chain leveraging PrintNightmare (CVE-2021-1675, CVE-2021-34527, and CVE-2021-36958) and FortiGate (CVE-2018-13374 and CVE-2018-13379) vulnerabilities to compromise unpatched systems.
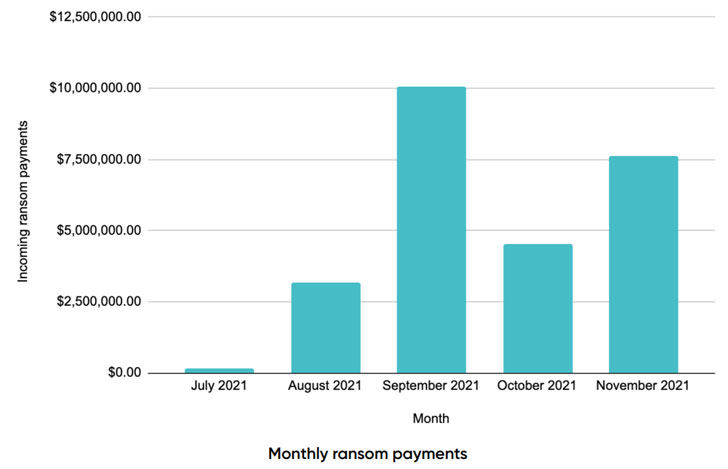
Conti came to light in October 2019 and is believed to be the work of a Russia-based threat group called Wizard Spider which doubles as the operator of the infamous TrickBot banking malware. Well over 500 different companies have had their business-critical data exposed and also receiving over 500 bitcoin ($26 million) in payments since July 2021.
Upon analysis of ransomware samples and bitcoin wallet addresses utilized for receiving payments have revealed connections between Conti and Ryuk with both families relying on TrickBot, Emotet and BazarLoader for delivering file-encrypting payloads onto the victims network via email phishing and a host of other social engineering schemes.
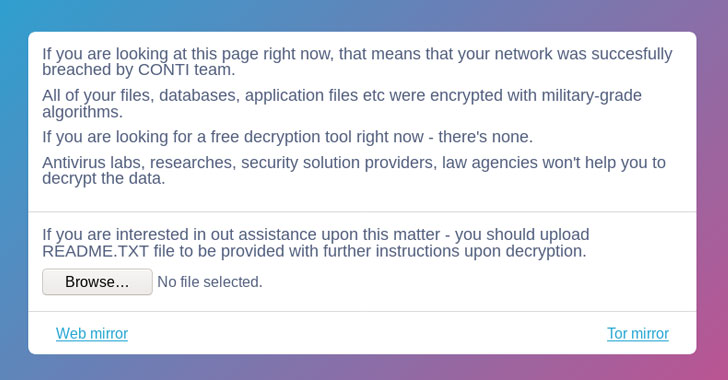
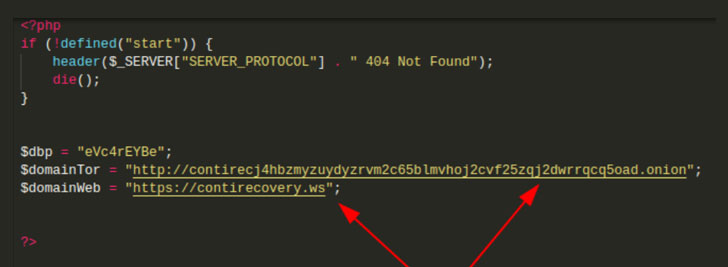
PRODAFT said it was also able to gain access to the group’s recovery service and an admin management panel hosted as a Tor hidden service on an Onion domain, revealing extensive details of a clearnet website called “[contirecovery[.]ws]” that contains instructions for purchasing decryption keys from the affiliates. Interestingly, an investigation into Conti’s ransomware negotiation process published by Team Cymru last month highlighted a similar open web URL named “contirecovery[.]info.”