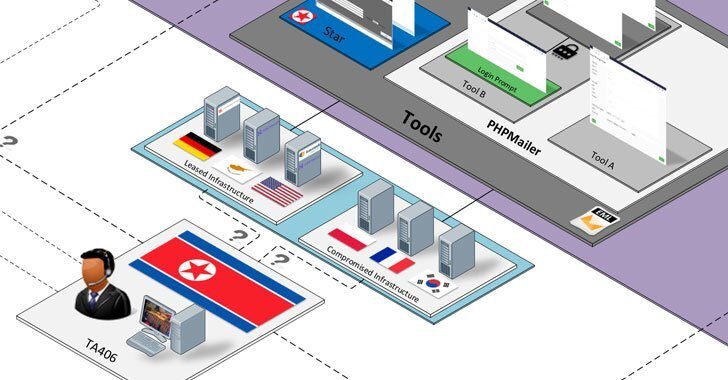
Enterprise security firm Proofpoint has linked TA406, a North Korean threat actor to a wave of credential theft campaigns targeting research, education and government with two of the attacks aimed at distributing malware which could be used for intelligence gathering.
TA406 also known as Kimsuky came into operations as early as 2012 emerging as one of the most active advanced persistent threat group (APT) group which has been observed for setting its sights on cyber espionage as well as conducting attacks for financial gains with its target being government entities, think tanks and individuals identified as experts in various fields as well as harvests sensitive information pertaining to foreign policy and national security issues.
“Like other APT groups that constitute a big umbrella, Kimsuky contains several clusters: BabyShark, AppleSeed, Flower Power, and Gold Dragon,” Kaspersky researchers noted in their Q3 2021 APT trends report published last month. The AppleSeed sub-group is also referred to as TA408.
The group also employs convincing social engineering schemes and watering hole attacks to get more targets before sending them malware-infected payloads, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said in a public alert issued in October 2020.
Researchers at Cisco Talos earlier this month, disclosed an ongoing Kimsuky campaign since June 2021 that was found leveraging malicious blogs hosted on Google’s Blogger platform to target high-value South Korean targets, including geopolitical and aerospace research agencies, while delivering a “constantly evolving set of implants derived from the Gold Dragon/Brave Prince family” that act as file exfiltrators, information gatherers, and credential stealers for reconnaissance, espionage, and credential harvesting.
“This campaign begins with malicious Microsoft Office documents (maldocs) containing macros being delivered to victims,” Talos researchers explained. “The infection chain results in the malware reaching out to malicious blogs set up by the attackers. These blogs provide the attackers the ability to update the malicious content posted in the blog depending on whether a victim is of value to the attackers.”
The threat actors simultaneously commenced weekly email threat using the identity of legitimate policy experts, while it featured themes related to nuclear weapon, politics and Korean foreign policy luring targeted individuals to give up corporate credentials via a rogue URL embedded in the messages that redirect the victims to custom credential-harvesting pages.
Kimsuky’s phishing campaigns had a noticeable shift in March 2021 when the emails moved beyond credential theft to become a medium for distributing malware, coinciding with North Korea’s missile tests conducted later that month.
The emails included a link that sent the target to an attacker-controlled domain used to trick targets into downloading a compressed archive incorporating a binary, which is orchestrated to create a scheduled task that is executed every 15 minutes to install additional malware from a remote server. However, the ultimate motive behind the attacks remains unclear as no follow-on payloads were observed.
Another notable attack in June resulted in the deployment of a downloader (“FatBoy”) using an HTML attachment lure that was then used to retrieve a next-stage reconnaissance script capable of collecting “extensive information” about the targeted device. Proofpoint said that both the campaigns exhibited overlaps with attacks previously identified as mounted by the Konni Group.
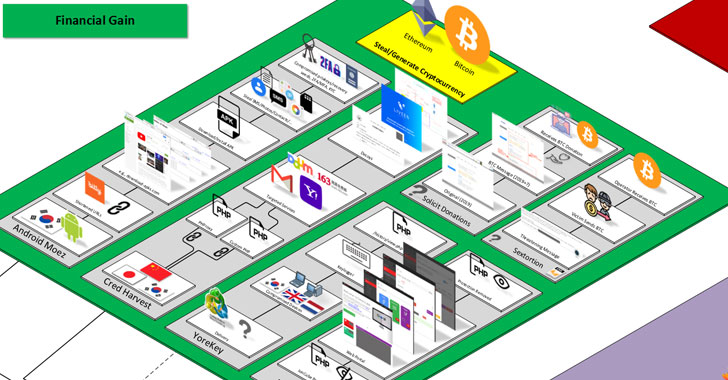
Other notable tools in its malware arsenal encompass a Windows keylogger dubbed YoreKey, a number of rogue Android apps striking cryptocurrency users in South Korea, a deobfuscation service named Deioncube to decode files encrypted with ionCube’s source code protection software, and a sextortion scam that urges email recipients to transfer an amount worth $500 in bitcoin to a valid wallet associated with a South Korea-based NGO.
“It’s unknown whether the NGO was compromised, and the donation message was placed on their website maliciously, or if there’s another explanation,” the researchers said. “As of June 2021, the associated bitcoin wallet had received and sent about 3.77 bitcoin.”