Hackers are putting in efforts to exploit a recently disclosed privilege escalation vulnerability in order to execute arbitrary codes on fully-patched systems. Tracked as CVE-2021-42379 the elevation of privilege flaw affects Windows Installer software component and was originally resolved as part of Microsoft’s Patch Tuesday updates for November 2021.
Researchers have indicated that it was not only impossible to bypass the fix implemented by Microsoft but also achieve local privilege escalation via a newly discovered zero-day bug.
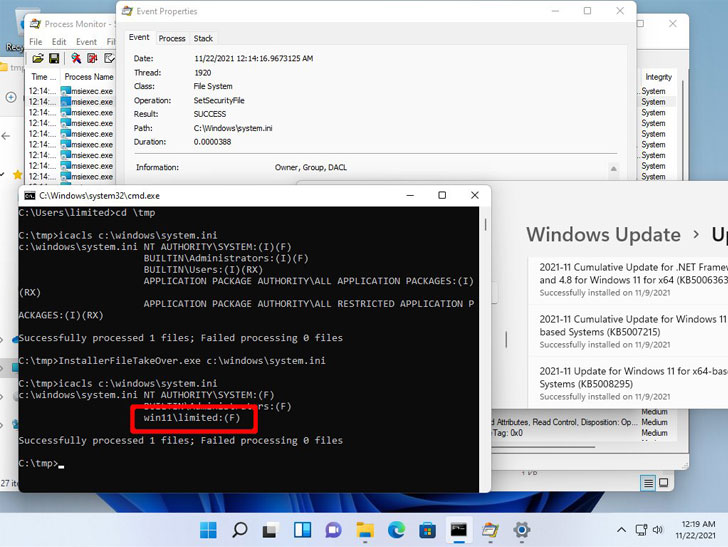
This takes place by overwriting the discretionary access control list (DACL) for Microsoft Edge Elevation Service to replace any executable file on the system with an MSI installer file, allowing an attacker to run code with SYSTEM privileges.
Having admin privileges, the attacker could abuse the access to gain full control over the compromised system including ability to download additional software delete and exfiltrate senstive information stored in the machine.
“Can confirm this works, local priv esc. Tested on Windows 10 20H2 and Windows 11. The prior patch MS issued didn’t fix the issue properly,” tweeted security researcher Kevin Beaumont, corroborating the findings.
Researchers acknowledge that this latest variant of CVE-2021-41379 is more powerful than the original one and the best course of action is to wait for Microsoft to release a security patch for the problem as this vulnerability is a complex one.
Microsoft is yet to act on the public disclosure nor release a fix when updates are released we would update the story.