Air-gapped networks have been discovered to be attacked by four different malicious frameworks bringing the total number of such toolkits to 17 and offering adversaries a pathway to cyber espionage and exfiltrate classified information.
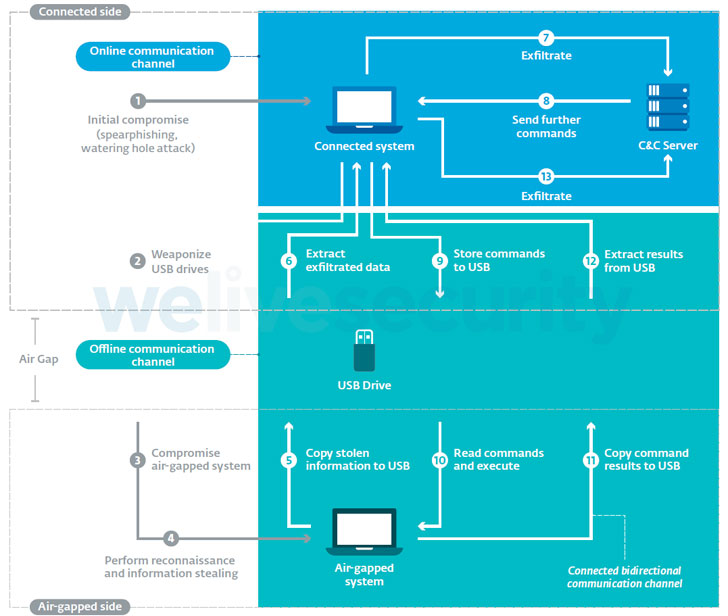
Researchers have stated that the frameworks were designed to perform some form of espionage and they all used USB drives as physical transmission medium to transfer data in and out of the targeted air-gapped network.
Air-gapping is a security measure which prevents unauthorized access to systems by physically isolating them from other unsecured networks including local area networks. The only possible way to transfer data is by connecting a physical device to it e.g USB drive or external hard disks.
Given that the mechanism is one of the most common ways SCADA and industrial control systems (ICS) are protected, APT groups that are typically sponsored or part of nation-state efforts have increasingly set their sights on the critical infrastructure in hopes of infiltrating an air-gapped network with malware so as to surveil targets of interest.
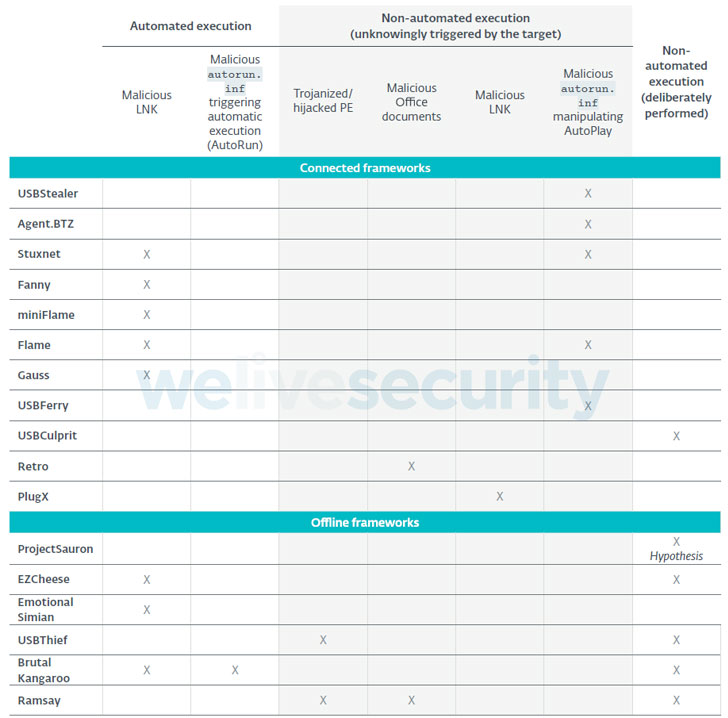
They are built to attack Windows-based operating systems, cybersecurity researchers have stated that no fewer than 75% of all the frameworks were found leveraging LNK or AutoRun files on USB drives to either carry out initial compromise of the air gapped system or to move laterally within the air gapped network.
Some frameworks that have been attributed to well-known threat actors are as follows —
USBStealer (APT28 aka Sednit, Sofacy, or Fancy Bear)
Retro (DarkHotel aka APT-C-06 or Dubnium)
Ramsay (DarkHotel)
USBCulprit (Goblin Panda aka Hellsing or Cycldek)
Each framework has devised its own way but they all use weaponized USB drives.
Organizations with critical information systems are recommended to prevent direct email access on connected systems, disable USB ports and sanitize USB drives as well as carry out periodic analysis of air-gapped systems for any sign of suspicious activity.