A new form of malware hits E-commerce platforms in the U.S., Germany and France this malware is said to be targeting Nginx servers in an attempt to masquerade its presence and slip past detection by security solutions.
Sansec Threat Research team have stated in a recent report that “this novel code injects itself into a host Nginx application and is nearly invisible….. The parasite is used to steal data from eCommerce servers, also known as ‘server-side Magecart.'”
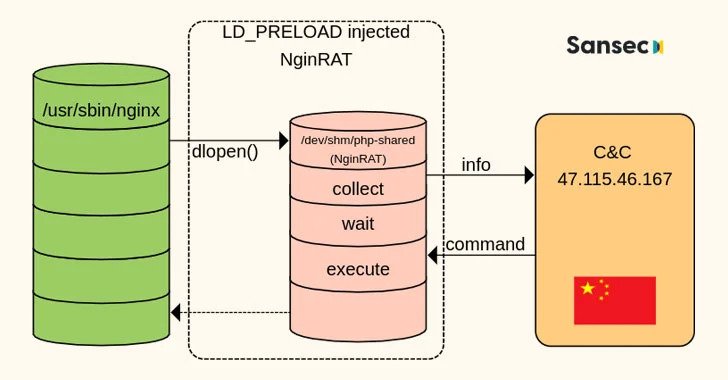
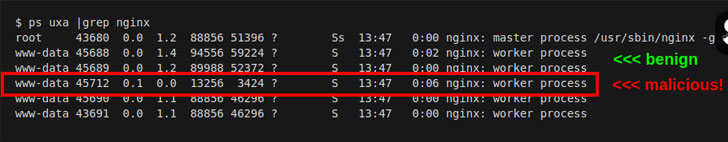
Nginx is a free and open-source software which could also be used as a reverse proxy, load balancer, mail proxy and HTTP cache. NginRAT, as the malware is called, works by hijacking a host Nginx application to embed itself into the webserver process.
The trojan itself is delivered via CronRAT, another piece of malware the Dutch cybersecurity firm disclosed last week as hiding its malicious payloads in cron jobs scheduled to execute on February 31st, a non-existent calendar day.
Both CronRAT and NginRAT are designed to provide a remote way into the compromised servers, wit the aim of intrusion being to make server-side modifications to the compromised e-commerce websites in a manner enabling exfiltration of data by skimming online payment forms.
The attacks, are the work of a cybercrime syndicate comprised of dozens of subgroups that are involved in digital credit card theft by exploiting software vulnerabilities to gain access to an online portal’s source code and insert malicious JavaScript code that siphons the data shoppers entries into checkout pages.
Researchers have noted that skimmer groups are increasing in number and targeting various e-commerce platforms with the use of various ways to remain undetected.