The wiper malware which attacked dozens of Ukranian agencies earlier this month has been analysed thus revealing “strategic similarities” to NotPetya malware that was unleashed against the country’s infrastructure and elsewhere in 2017.
WhisperGate as it is been called was discovered by Micrfosoft last week, which said it observed the destructive cyber campain targeting government, non-profit, and information technology entities in the nationm attributing the intrusion to an emerging threat cluster codenamed “DEV-0586.”
Cisco Talos in a report detailing its response efforts stated that, “While WhisperGate has some strategic similarities to the notorious NotPetya wiper that attacked Ukranian entities in 2017, including masquerading as ransomware and targeting and destroying the master boot record (MBR) instead of encrypting it, it notably has more components designed to inflict additional damage.”
Going on to state that stolen credentials were likely used in the attack. Threat actors were also said to have access to some of the victim networks month in advance before the infiltrations took place, a classic sign pf sophisticated APT attacks.
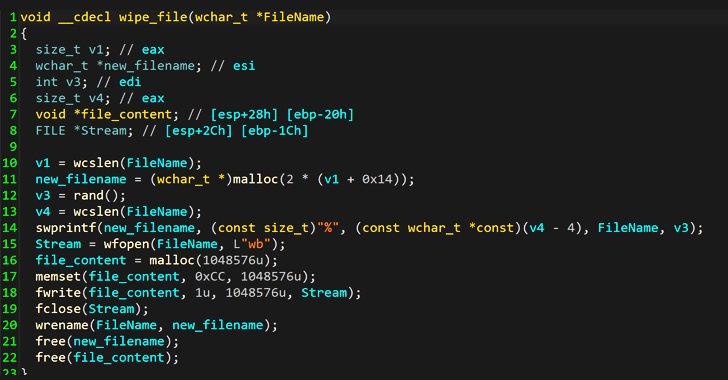
Whispergate’s infection chain is made as a multi-stage process that downloads a payload that wipes the master boot record (MBR), and afterwards downloads a malicious DLL file hosted on a Discord server, which drops and executes another wiper payload which irrevocably destroys files by overwriting their content with fixed data on the infected hosts.
These discoveries are coming a week after roughly 80 Ukrainian government agencies websites were defaced with Ukranian intelligence agencies confirming that the twin incidents are part of a wave of malicious activities targeting its critical infrastructure, as well as also noting that the attacks leveraged the recently disclosed Log4j vulnerabilities to gain access to some of the compromised systems.
Wired’s Andy Greenberg is quoted stating that “Russia is using the country as a cyberwar testing ground — a laboratory for perfecting new forms of global online combat.”
Talos researchers have also stated that “Systems in Ukraine face challenges that may not apply to those in other regions of the world, and extra protections and precautionary measures need to be applied, making sure those systems are both patched and hardened is of the utmost importance to help mitigate the threats the region faces.”