A new campaign that uses password cracking software to grab control of Programmable Logic Controllers (PLCs) and coax the devices into becoming part of a botnet is aimed at industrial engineers and operators.
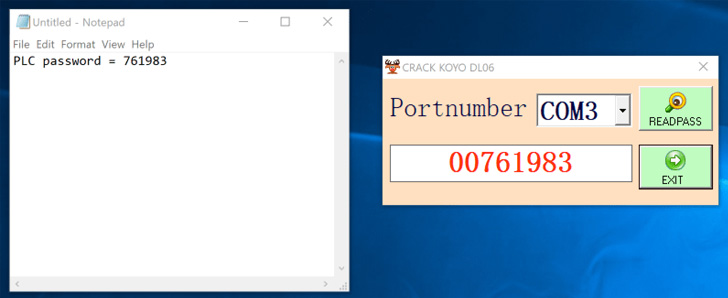
According to Dragos security researcher Sam Hanson, the malware “exploited a flaw in the firmware which allowed it to extract the password on demand.” Furthermore, the programme was a malware dropper that infected the computer with the Sality malware and converted the host into a peer in the Sality peer-to-peer botnet.
The password recovery exploit built into the malware dropper, according to the industrial cybersecurity company, is intended to retrieve the credentials for the Automation Direct DirectLOGIC 06 PLC.
The vulnerability, identified as CVE-2022-2003 (CVSS score: 7.7), has been described as a case of sensitive data being transmitted in cleartext, which could result in data leakage and unauthorised alterations. In firmware Version 2.72, which was published last month, the problem was fixed.
The infections culminate in the deployment of the Sality virus, which performs distributed activities like password cracking and cryptocurrency mining while taking precautions to avoid detection by turning off security software operating on the affected workstations.
Additionally, the artefact found by Dragos has a crypto-clipper payload that substitutes the attacker’s wallet address for the original wallet address recorded in the clipboard to steal bitcoin during a transaction.
Not only Automation Direct, but also Omron, Siemens, ABB Codesys, Delta Automation, Fuji Electric, Mitsubishi Electric, Schneider Electric’s Pro-face, Vigor PLC, Weintek, Rockwell Automation’s Allen-Bradley, Panasonic, Fatek, IDEC Corporation, and LG are reportedly included in the tools’ list of vendors that are affected.
Hanson said, attributing the attacks to a potentially financially motivated adversary, “In general, it looks there is an ecosystem for this type of malware.” There are numerous social media profiles and websites that all advertise password “crackers.”
The targeting of operational technology (OT) networks by malicious malware is not new. In October 2021, Mandiant revealed how a range of viruses, including Sality, Virut, and Ramnit, among others, are compromising legal portable executable programmes.