Numerous bogus programmes that were discovered spreading the Joker, Facestealer, and Coper malware families through the online store have been removed by Google (SEE: HOW HACKERS HACK ANDROID PHONES).
Although the Android shop is regarded as a reliable resource for finding and installing apps, malicious actors have frequently found ways to get around Google’s security measures in an effort to trick unwary users into downloading malware-filled apps.
No different are the most recent Zscaler ThreatLabz and Pradeo discoveries. According to a paper released on Monday by researchers Viral Gandhi and Himanshu Sharma, “Joker is one of the most well-known malware families targeting Android smartphones.”
Despite widespread knowledge of this specific virus, it continues to enter Google’s official app store by frequently changing its trail signatures, including revisions to the malware’s code, execution procedures, and payload-retrieving strategies.
The software known as Joker (also known as Bread) is classified as fleeceware and is made to phone premium numbers, send SMS messages, and subscribe users to unwanted commercial services. In the Play Store, it was first noticed in 2017.
The two cybersecurity companies discovered a total of 53 Joker downloading apps, with the apps having been downloaded more than 330,000 times overall. These apps frequently pretend to be SMS, photo editors, blood pressure monitors, emoji keyboards, and translation tools before requesting privileged access to the device in order to function.
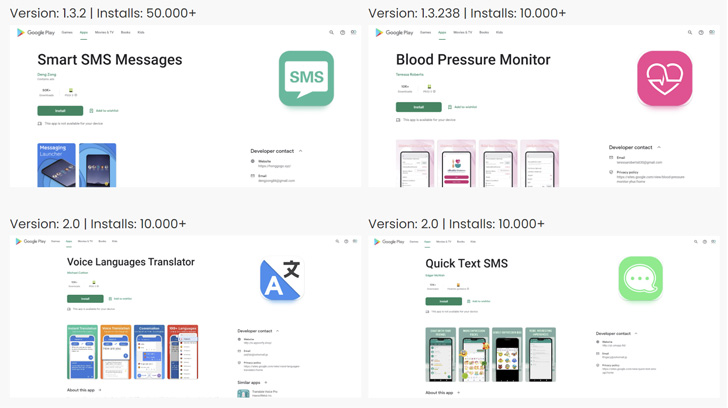
“The Joker developers have switched to hiding the malicious payload in a common asset file and packaging applications using commercial packers instead of waiting for apps to accumulate a certain number of installs and reviews before switching for a malware-laced version, the researchers explained the new strategy adopted by the persistent malware to avoid detection.
Joker isn’t the only malware out there; last week, security researcher Maxime Ingrao revealed eight additional apps that had Autolycos, a distinct strain of the malware that had amassed over three million downloads before being removed from the app store after more than six months.
What is novel about this type, according to Malwarebytes researcher Pieter Arntz, is that it is no longer dependent on a WebView. “The likelihood that the user of an impacted device detects something is off is significantly decreased by not requiring a WebView. By processing URLs on a remote browser and including the results in HTTP requests, Autolycos avoids WebView.”
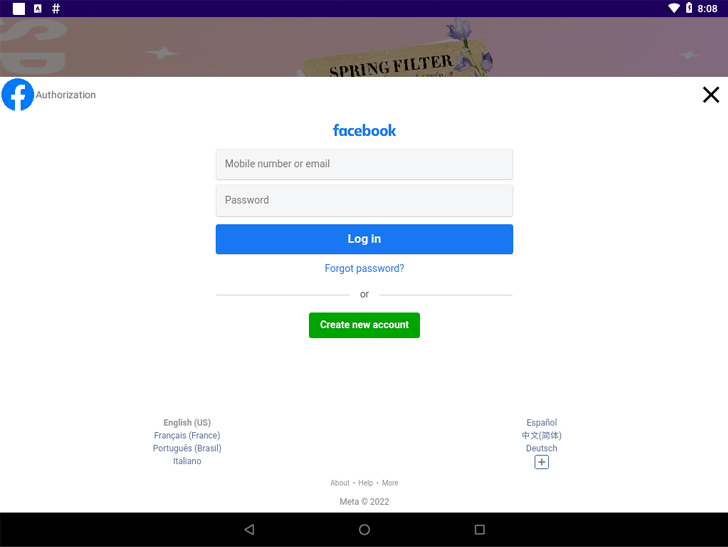
Also discovered in the official marketplace were apps embedding Facestealer and Coper malware. While the former enables the operators to siphon Facebook credentials and auth tokens, Coper — a descendant of the Exobot malware — functions as a banking trojan that can steal a wide range of data.
According to the researchers, Coper “is capable of intercepting and sending SMS text messages, making USSD (Unstructured Supplementary Service Data) requests to send messages, keylogging, locking/unlocking the device screen, performing overly attacks, preventing uninstalls, and generally allowing attackers to take control and execute commands on infected devices via remote connection with a C2 server.”
Like other banking trojans, the malware is infamous for abusing Android’s accessibility permissions to take complete control of the victim’s phone. The following is a list of Facestealer and Coper dropper apps:
- Vanilla Camera (cam.vanilla.snapp)
- Unicc QR Scanner (com.qrdscannerratedx)
If anything, the discoveries highlight Google’s long history of fighting to keep such spyware and fleeceware programmes out of its mobile app store, in part because threat actors have developed a variety of new techniques to remain undetected.
In addition to the standard best practises for installing apps from app stores, users are advised to avoid giving apps unauthorised access and to confirm the legitimacy of the apps they download by looking up developer information, reading reviews, and carefully reviewing their privacy policies.

