The threat actor responsible for the attack on Twilio and Cloudflare earlier this month has been connected to a larger phishing operation that targeted 136 businesses and led to a total of 9,931 accounts being compromised.
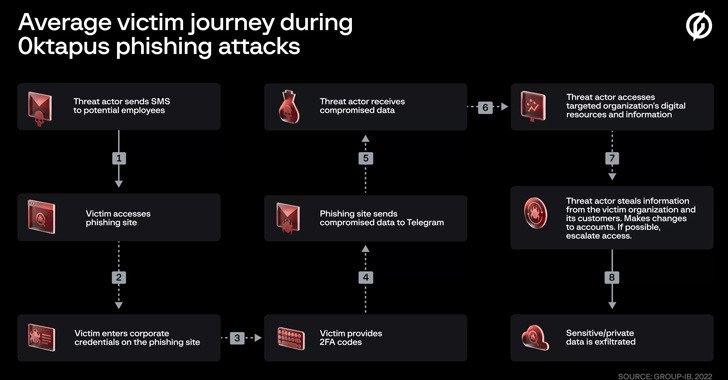
Because the primary intent of the assaults was to “get Okta identity credentials and two-factor authentication (2FA) codes from users of the targeted organizations,” the conduct has been denounced by Group-IB.
The Singapore-based corporation said the opponent sought out employees of businesses that use Okta, a provider of identity services, and praised the attacks for being well planned and carried out.
Targets were sent text messages with links to phishing websites that looked like the Okta authentication pages of the specific targeted entities.
According to Group-IB, “This instance is interesting because it was able to compromise a significant number of well-known businesses while using low-skill approaches.” Furthermore, once they had gained access to an organization, the attackers were able to instantly change directions and undertake supply chain strikes, showing that the attack had been properly thought out in advance.
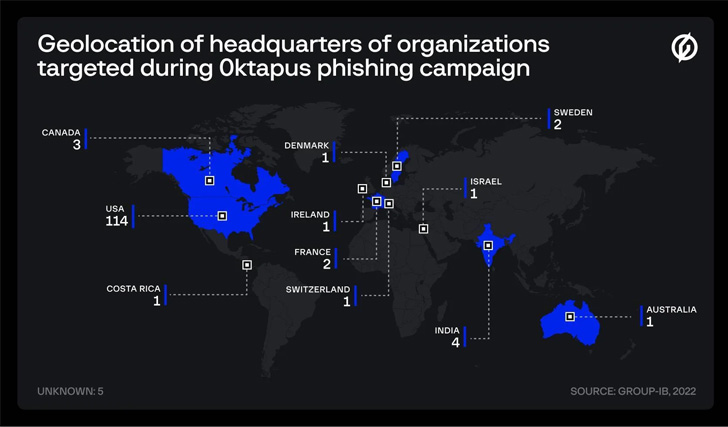
According to reports, at least 169 different phishing domains have been created for this purpose, with the majority of the victim organizations being based in the United States (114), India (4), Canada (3), France (2), Sweden (2), and Australia (1), among other countries. These websites shared a commonality in that they each made use of an undocumented phishing kit.
Software companies make up the majority of the affected businesses, followed by those in the telecom, business services, banking, education, retail, and logistics industries. Along with Twilio and Cloudflare, other confirmed victims include MailChimp and Klaviyo.
The organizations AT&T, KuCoin, Mailgun, Metro PCS, Slack, T-Mobile, and Verizon were also targeted, according to an examination of the 0ktapus phishing websites. Later supply chain attacks against Signal (through Twilio) and DigitalOcean used these beaches as a launching point (via MailChimp).
The assaults are noteworthy because they disseminated the compromised data, which included user credentials, email addresses, and multi-factor authentication (MFA) codes, over a Telegram channel that was under the control of an actor.
One of the channel administrators who goes by the alias X, according to Group-IB, was connected to a Twitter and GitHub account that suggests the person may be based in the American state of North Carolina.
Although the campaign’s ultimate goals are still unknown, it is believed to be espionage- and financially-motivated, giving the threat actor access to private information, proprietary information, and corporate inboxes as well as the ability to steal money.
Additionally, the attempts to get into Signal accounts suggest that the attackers are also attempting to obtain sensitive information such as private conversations. It is yet unknown how the hackers managed to get access to employee names and phone numbers.
While the threat actor may have struck lucky, Roberto Martinez, a Group-IB analyst, believes it is more likely that they deliberately organized their phishing campaign to undertake sophisticated supply chain attacks.
“The extent to which the attacks were preplanned from beginning to end or whether tactical decisions were made at various stages is still unknown. Whatever the case, the 0ktapus campaign has been a huge success; nevertheless, its entire scope might not be realized for some years.”