It has been discovered that a well-known Windows information stealer by the name of ViperSoftX is used to spread a malicious extension for web browsers based on the Chromium operating system.
Due to its standalone features that allow it to track website visits, steal login information and clipboard contents, and even swap cryptocurrency addresses via an adversary-in-the-middle (AiTM) attack, the rogue browser add-on was given the name VenomSoftX by a cybersecurity company based in the Czech Republic.
Fortinet described ViperSoftX, which initially surfaced in February 2020, as a JavaScript-based remote access trojan and cryptocurrency stealer. Sophos threat analyst Colin Cowie first noted the malware’s use of a browser extension to promote its information-gathering objectives last year.
According to a technical write-up by Avast researcher Jan Rubn, “This multi-stage stealer demonstrates interesting concealing skills, camouflaged as little PowerShell scripts on a single line in the middle of otherwise innocent-looking big log files, among others.”
ViperSoftX focuses on stealing cryptocurrency, changing the clipboard, fingerprinting the infected machine, as well as downloading and running arbitrary extra payloads or issuing commands.
Cracked versions of Microsoft Office and Adobe Illustrator that are uploaded on file-sharing websites are frequently used as the vector for spreading ViperSoftX.
In addition to a clean copy of the cracked program, the downloaded executable file also contains other files that enable persistence on the host and contain the ViperSoftX PowerShell script.
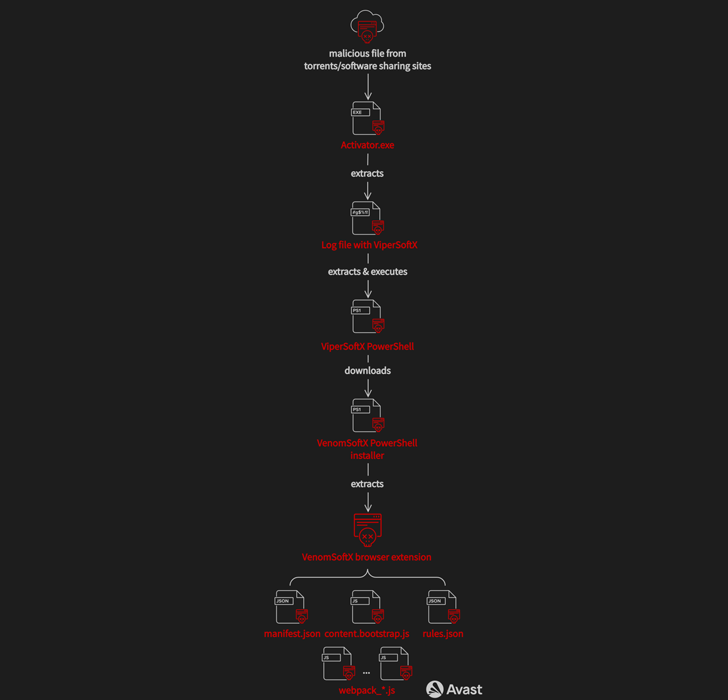
ViperSoftX focuses on stealing cryptocurrency, changing the clipboard, fingerprinting the infected machine, as well as downloading and running arbitrary extra payloads or issuing commands.
Cracked versions of Microsoft Office and Adobe Illustrator that are uploaded on file-sharing websites are frequently used as the vector for spreading ViperSoftX.
In addition to a clean copy of the cracked program, the downloaded executable file also contains other files that enable persistence on the host and contain the ViperSoftX PowerShell script.
It’s important to note that ChromeLoader, a different browser-based information thief, also employs the —load-extension technique (aka Choziosi Loader or ChromeBack).
Similar to ViperSoftX, VenomSoftX is designed to steal cryptocurrency from its victims. However, VenomSoftX tampers with API requests to cryptocurrency exchanges in order to siphon off the digital assets, unlike the latter, which acts as a clipper to redirect payment transfers to an attacker-controlled wallet.
The addon specifically targets the following services: Blockchain.com, Binance, Coinbase, Gate.io, and Kucoin.
The change adds a new layer of complexity to the practice of exchanging clipboards, but it doesn’t immediately arouse suspicion because the wallet address is changed at a much more fundamental level.
Avast reported that since the beginning of 2022, it has found and stopped over 93,000 infections, with the majority of the affected users being found in India, the U.S., Italy, Brazil, the U.K., Canada, France, Pakistan, and South Africa.
According to a study of the samples’ hard-coded wallet addresses, as of November 8, 2022, the operation has earned its creators a total of around $130,421 in different cryptocurrencies. Since then, the total financial benefit has decreased to $104,500.
Since blockchain/ledger transactions are fundamentally irreversible, when a user later reviews the payment history, it is already too late, according to Rubn.

