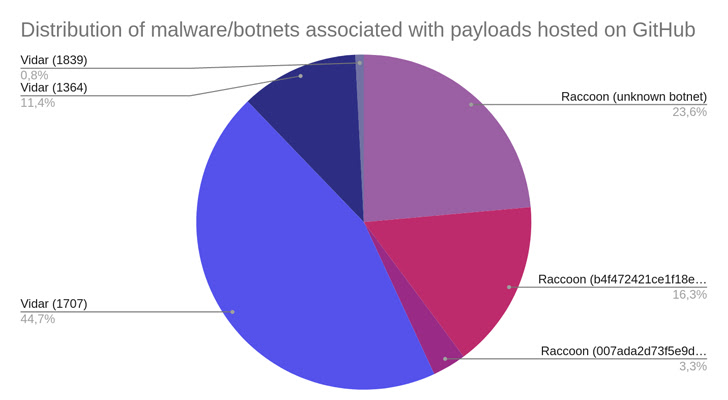
Since early 2020, information-stealing malware like Raccoon and Vidar has been disseminated using a “large and resilient infrastructure” made up of over 250 domains.
Security company SEKOIA stated in a research released earlier this month that the infection chain “uses roughly a hundred of phoney cracked software catalogue websites that lead to multiple links before downloading the payload located on file share networks, such as GitHub.”
The domains were determined by the French cybersecurity firm to be run by a threat actor with a traffic direction system (TDS) that other cybercriminals can hire to disseminate their malware.
The attacks target people who use search engines like Google to look for cracked versions of software and video games, surfacing bogus websites on top and tricking people into downloading and running the harmful payloads by using a tactic called search engine optimization (SEO) poisoning.
A download link for the promised software is included in the poisoned result, and clicking it starts a five-stage URL redirection process that sends the user to a page with a shortened link that goes to a password-protected RAR archive file housed on GitHub and its password.
Multiple redirections make automated analysis by security solutions more difficult, according to the researchers. It is probably certainly intended to ensure resilience by carving the infrastructure in such a way that it is simpler and faster to update or replace a phase.
Either of the two malware families, Raccoon or Vidar, are installed on the system should the victim uncompress the RAR archive and launch the supposed setup programme that it contains.
The news comes as Cyble revealed a fraudulent Google Ads campaign that uses popular programmes like AnyDesk, Bluestacks, Notepad++, and Zoom as enticements to distribute Rhadamanthys Stealer, a stealer with a tonne of features.
A further variation of the attack chain has been seen using phishing emails that pretend to be bank statements to trick unwary users into clicking on malicious links.
In the past, fake websites pretending to be the well-known remote desktop programme have been used to spread Mitsu Stealer, a Python-based information thief.
Both kinds of malware are capable of extracting a variety of personal data from infected computers, gathering login information from web browsers, and stealing information from different cryptocurrency wallets.
Users are encouraged to avoid installing illegal software and, whenever possible, to use multi-factor authentication to secure their accounts.
The researchers advised users to use caution when opening spam emails or visiting phishing websites and to double-check the source before downloading any software.