The threat actors have responded with an upgraded version of ESXiArgs ransomware that encrypts more data after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a decryptor for affected victims to recover from ESXiArgs ransomware attacks.
A system administrator posted information on the new variant on an online forum where another user said that files greater than 128 MB will have 50% of their data encrypted, making the recovery process more difficult.
Another significant modification is the removal of the Bitcoin address from the ransom message; instead, the attackers now advise victims to get in touch with them on Tox to get the wallet information.
In a blog post, Censys stated that the threat actors “realised that researchers were tracking their payments, and they may have even known before they launched the ransomware that the encryption procedure in the initial variant was reasonably straightforward to defeat.”
They are, in other words, watching.
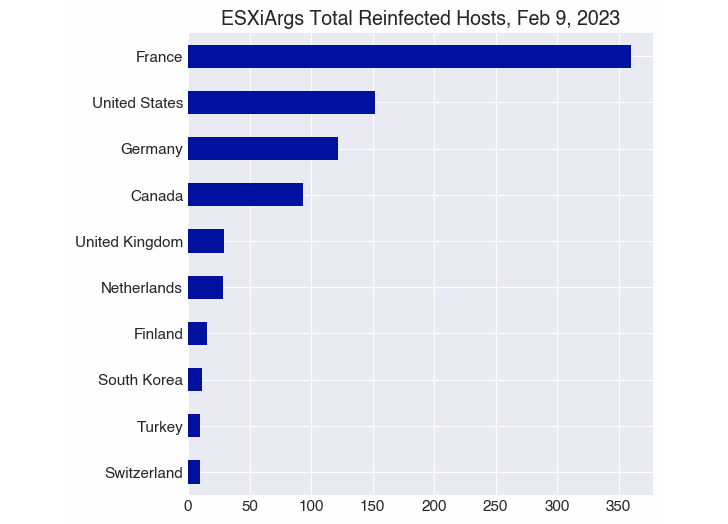
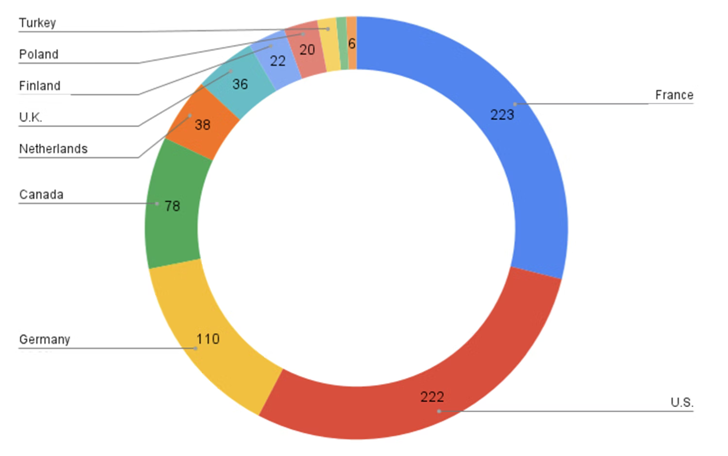
As of February 9, 2023, 1,252 servers—1,168 of which are reinfections—had contracted the current version of ESXiArgs, according to statistics given by the crowdsourced portal Ransomwhere.
Over 3,800 different hosts have been affected since the ransomware epidemic first appeared in early February. France, the United States, Germany, Canada, the United Kingdom, the Netherlands, Finland, Turkey, Poland, and Taiwan are home to the majority of the illnesses.
ESXiArgs is built on the Babuk locker, whose source code was exposed in September 2021, along with Cheerscrypt and PrideLocker. However, a key feature that sets it apart from other ransomware families is the lack of a data leak site, which shows that it doesn’t operate using the ransomware-as-a-service (RaaS) paradigm.
According to cybersecurity firm Intel471, ransoms are set at just over two bitcoins (about $47,000 USD) and victims have three days to pay.
Although it was initially believed that the incursions entailed the misuse of a now-patched, two-year-old OpenSLP flaw in VMware ESXi (CVE-2021-21974), there have been reports of compromises in devices with the network discovery protocol turned off.
Since then, VMware has stated that it has not discovered any proof that the ransomware is being spread using a zero-day vulnerability in its software.
This suggests that the threat actors behind the activity may be taking advantage of a number of ESXi’s known vulnerabilities, therefore users must act immediately to update to the most recent version. The perpetrators of the attacks have not yet been identified as a recognised threat actor or organisation.
Arctic Wolf said that the effort is connected to a single threat actor or organisation “based on the ransom message.” Before carrying out an intrusion, “more established ransomware gangs generally conduct OSINT on possible victims and determine the ransom price depending on perceived worth.”
Rapid7, a cybersecurity firm, reported discovering 18,581 ESXi servers with internet access that are vulnerable to CVE-2021-21974, and it also noted RansomExx2 actors opportunistically targeting vulnerable ESXi servers.
According to Tony Lauro, head of security technology and strategy at Akamai, “cyber attackers continue to torment enterprises via death by a thousand cuts,” despite the apparent small financial impact of this particular hack.
“The ESXiArgs ransomware is a perfect illustration of both the need for system administrators to apply fixes as soon as they are made available and the extent attackers would go to in order to succeed in their attacks. Patching is only one type of defence you can use, though.”