After a seven month hiatus, the Russian-speaking cyber-espionage group RedCurl returns. With their arrival on the scene, the group has targeted 4 companies including a large retail store in Russia as well as improving on its toolset in an attempt to thwart analysis and antivirus detection.
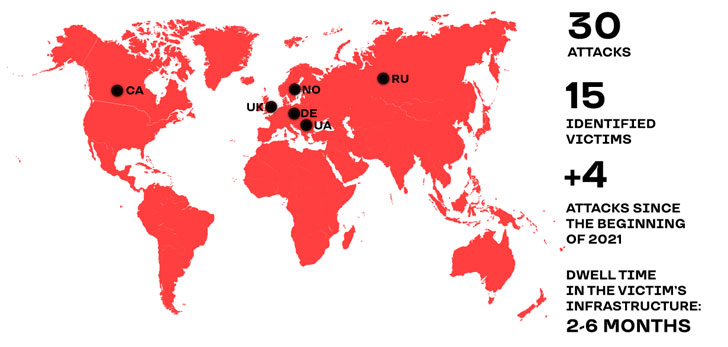
The group became active in November 2018 with attacks of up to 30 targets linked to the group all aimed at corporate cyber espionage and document theft against 14 organizations spanning construction, consulting, finance, retail, insurance, and legal sectors and located in the U.K., Germany, Russia, Ukraine, Canada and Norway.
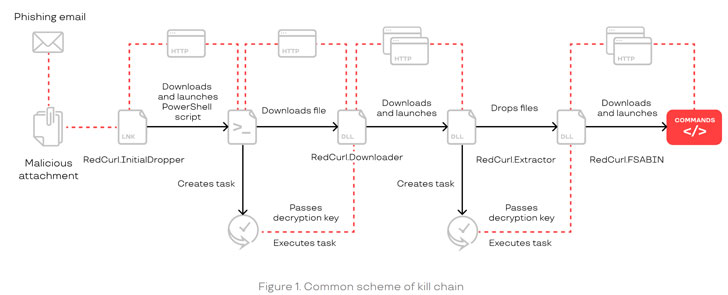
They have been observed to use different tools to infiltrate its targets and steal internal corporate documentation, such as staff records, legal files, and enterprise email history, with the collective spending anywhere from two to six months between initial infection to the time data gets actually stolen.
RedCurl’s mode of operation takes a different path from other adversaries not least because it doesn’t deploy backdoors nor rely on post-exploitation tools like CobaltStrike and Meterpreter, both of which are seen as typical methods to remotely control compromised devices. The group has not been observed conducting attacks that are motivated by financial gains and involve encrypting victim infrastructure or ransom demand for stolen data.
Rather they are more about obtaining valuable info as covertly as possible with a combination of self-developed and publicly available programs to gain access, perform footprinting, maintain persistence, move laterally and exfiltrate documents.
“Espionage in cyberspace is a hallmark of state-sponsored advanced persistent threats,” the researchers said. “In most cases, such attacks target other states or state-owned companies. Corporate cyber espionage is still a relatively rare and, in many ways, unique occurrence. However, it is possible that the group’s success could lead to a new trend in cybercrime.”