A new Android trojan has been observed to be distributed via the official Google Play Store with the goal of targeting 56 European banks and carrying out harvesting sensitive information from compromised devices.
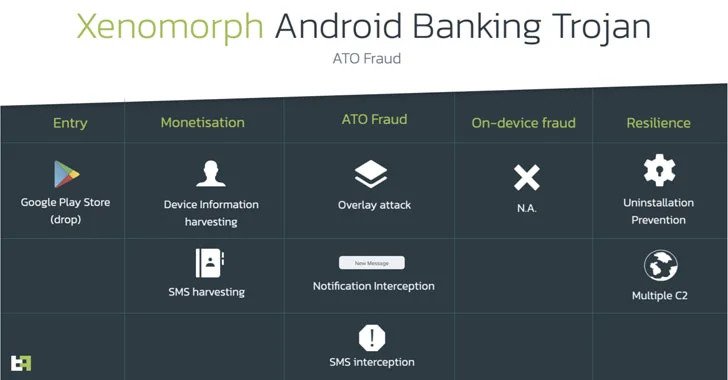
The trojan has been nicknamed Xenomorph and its noticed to share overlaps with another banking trojan tracked under the moniker Alien while also being “radically different” from its predecessor in terms of the functionalities offered. The malware has a detailed and modular engine to abuse accessibility services, which in the future could power very advanced capabilities, like ATS.
Alien arrived shortly after the demise of the infamous Cerberus malware in August 2020 and is said to possess features like notification sniffing and authenticator-based 2FA theft and other forks have been spotted in the wild including ERMAC in September 2021.
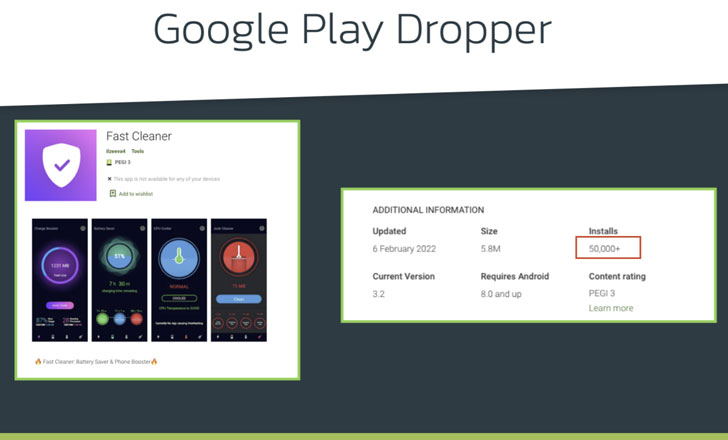
Xenomorph is another example of an Android banking trojan that is focused on circumventing Google Play Store’s security protections by masquerading as productivity apps such as “Fast Cleaner” deceiving unaware victims into installing the malware.
A fitness app dubbed GymDrop was also discovered to be delivering the Alien banking trojan payload in November by masking it as a “new package of workout exercises”. Fast Cleaner is still available on the app store and is popular in Portugal and Spain with the app making its first appearance in the Play Store towards the end of January 2022.
Reviews have also shown to come from users saying it is a malware and it asks for update to be confirmed continuously. Other users also noted that the app puts malware on devices and it also has a self-protection system so that you cannot uninstall it.
Xenomorph also uses the time-tested tactic of prompting the victims to grant it Accessibility Service privileges and abuse the permissions to conduct overlay attacks where the malware injects rogue login screen atop targeted apps to siphon credentials and other personal information.
Its notification interception feature extracts two-factor authentication token received via SMS, and acquire list of installed apps and this results are exfiltrated to a remote command-and-control server.
Xenomorph arrival shows that threat actors do not relent in creating malware apps and placing them in official markets. Criminals adopt different tactics to support their nefarious activities and we therefore cannot relent in our poise for a cyber secured space.