As many as seven vulnerabilities have been disclosed in PTC’s Axeda software which could be weaponized to access medical and IoT devices without authorization.
Popular known as Access:7, with weaknesses of which 3 are rated Critical in severity with the potential of affecting over 150 device models spanning over 100 different manufacturers which makes it a significant supply chain risk.
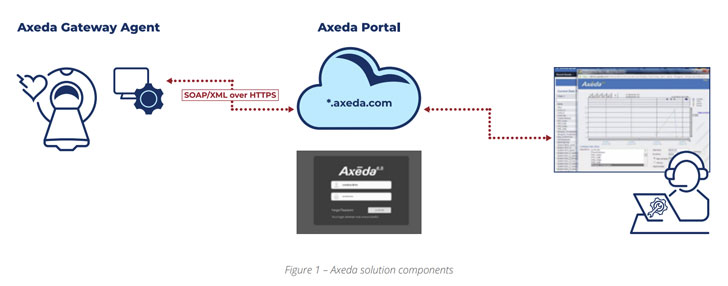
PTC Axeda provides solutions which comprise cloud platform that allow devices manufacturers to create connectivity to remotely monitor, manage and service a large number of connected machines, sensors and devices through what is called the agent, installed by the OEMs before the devices are sold to customers.
Access:7 enables hackers to remotely execute malicious code, gain access to sensitive data or modify configurations on medical and IoT devices running PTC’s Axeda remote code and management agent, researchers from Forescout and CyberMDX said in a joint report published today.
55% of the impacted vendors belong to the healthcare sector, followed by IoT (24%), IT (8%), financial services (5%), and manufacturing (4%) industries. At least 54% of the customers with devices running Axeda have been identified in the healthcare sector.
Other vulnerable devices include everything from ATMs, vending machines, label printers to barcode scanning systems, SCADA systems, asset monitoring, cash management systems, IoT gateways and industrial cutters.
The list of flaws are below –
CVE-2022-25246 (CVSS score: 9.8) – The use of hard-coded credentials in the AxedaDesktopServer.exe service that could enable remote takeover of a device
CVE-2022-25247 (CVSS score: 9.8) – A flaw in ERemoteServer.exe that could be leveraged to send specially crafted commands to obtain Remote code execution (RCE) and full file system access
CVE-2022-25251 (CVSS score: 9.4) – Missing authentication in the Axeda xGate.exe agent that could be used to modify the agent’s configuration
CVE-2022-25249 (CVSS score: 7.5) – A directory traversal flaw in the Axeda xGate.exe agent which could allow a remote unauthenticated attacker to obtain file system read access on the web server
CVE-2022-25250 (CVSS score: 7.5) – A denial-of-service (DoS) flaw in the Axeda xGate.exe agent by injecting an undocumented command
CVE-2022-25252 (CVSS score: 7.5) – A buffer overflow vulnerability in the Axeda xBase39.dll component that could result in a denial-of-service (DoS)
CVE-2022-25248 (CVSS score: 5.3) – An information disclosure flaw in the ERemoteServer.exe service that exposes the live event text log to unauthenticated parties
Upon successful exploitation of the flaws, the attacker is equipped with capabilities to remotely execute malicious codes which enables the attacker take full control of devices, access sensitive data, modify configurations and shut down specific services in the impacted devices.
This flaws affecting all versions of the Axeda Agent prior to 6.9.3, were reported to PTC on August 10, 2021 as part of a coordinated disclosure process that involved the U.S. Cybersecurity and Infrastructure Security Agency (CISA), Health Information Sharing and Analysis Center (H-ISAC), and the Food and Drug Administration (FDA).
Users are recommended to upgrade to Axeda agent version 6.9.1 build 1046, 6.9.2 build 1049, or 6.9.3 build 1051 in order to mitigate the flaws.
Security vulnerabilities have always been known to attack healthcare systems. In December 2020, CyberMDX disclosed “MDhex-Ray” a severe flaw in GE Healthcare’s CT, X-Ray, and MRI imaging products that could result in the exposure of protected health information.
Access:7 has been taken as a supply chain vulnerability as this affects a solution sold to device manufacturers that did not develop their in-house remote servicing system and this affects many downstream manufacturers and devices.