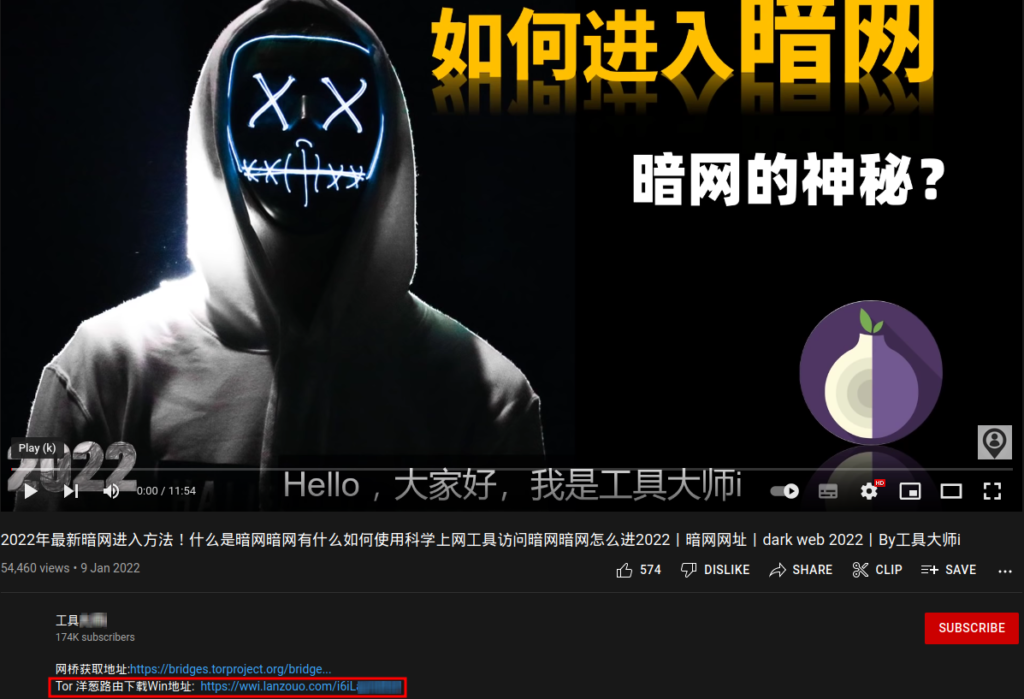
A trojanized Windows installer for the Tor Browser is being distributed through a well-known Chinese-language YouTube channel.
The campaign, OnionPoison, was named by Kaspersky, and all of the victims were in China. The scope of the attack is yet unknown, but the Russian cybersecurity firm reported that in March 2022, victims began to show up in its data.
A link found in the description of a video posted to YouTube on January 9, 2022 is used to spread the malicious version of the Tor Browser installation. To date, more than 64,500 people have viewed it.
The channel that is showing the video claims to be based in Hong Kong and has 181,000 members. As of this writing, the social networking platform still allows users to view the video.
The attack takes use of the fact that the legitimate Tor Browser website is prohibited in China to fool users into downloading the malicious copy when they are only looking for “Tor浏览器” (the word for Tor Browser in Chinese) on YouTube.
When a user clicks the link, a 74MB executable that is intended to store users’ browser histories and data entered into website forms is presented.
Leonid Bezvershenko and Georgy Kucherin, researchers for Kaspersky, noted that one of the libraries included with the malicious Tor Browser is contaminated with spyware that gathers various types of personal information and transmits it to a command-and-control server.
This is done via the armed freebl3.dll library making contact with a remote server, which replies with a second-stage payload containing the spyware, but only if the victim’s IP address is Chinese.
The spyware module also has the ability to conduct arbitrary shell commands on the victim’s computer and exfiltrate a list of installed programs and active processes, browser histories, WeChat and QQ account IDs, and browsing histories.
The command-and-control server (torbrowser[.]io) is unique since it looks just like the original Tor Browser website and has download buttons that take users to the official Tor Browser portal.
The development is similar to another operation where YouTube videos with links to harmful archive files distributing information thieves and cryptocurrency miners are shown to players looking for cheats and cracks. The compromised channels have now been deleted by Google.
The Hacker News has contacted the internet behemoth for comment regarding the most recent discoveries, and if we hear back, we’ll update the story.