In yet another indicator of how hacking groups are quick to capitalize on world events and improvise their attack campaigns for maximum impact, threat actors have been discovered impersonating Amnesty International to distribute malware that purports to be a security software designed to safeguard against NSO Group’s Pegasus surveillanceware.
Hacking groups have never failed at capitalizing on world events to improvise their attacks for greater impact. In the recent event of things, threat actors have been discovered to be impersonating Amnesty International and spreading malware purporting to be security software aimed at safeguarding against NSO Group’s Pegasus surveillanceware.
This has been achieved by the Hackers setting up a phony website that looks like Amnesty International – a human rights-focused non-governmental organization – and points to a promised antivirus tool to protect against the NSO Group’s Pegasus tool. However upon downloading, it installs a little-known Sarwent malware.
Affected countries include U.K, the U.S., Czech Republic, Colombia and Romania. It has not yet been stated as to how victims were tricked into visiting the fake Amnesty International website however it is believed that persons affected could be users who went in search for protection against this threat.
The development comes on the heels of an explosive investigation in July 2021 that revealed widespread abuse of the Israeli company’s Pegasus “military-grade spyware” to facilitate human rights violations by surveilling heads of state, activists, journalists, and lawyers around the world. The NGO has since also released a Mobile Verification Toolkit (MVT) to help individuals scan their iPhone and Android devices for evidence of compromise.

Apart from social engineering tricks by designing an identical website, the mode of operation aims to trick visitors into downloading an “Amnesty Anti Pegasus Software” disguised as an antivirus tool featuring capabilities to enable the hacker find a remote way into the compromised machine and get sensitive information such as login credentials.
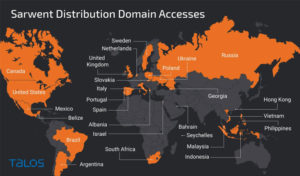
Russian-speaking actors have been identified as the major suspects by Cybersecurity researchers who they also suspect to be responsible for the Sarwent backdoor which has been in action since January 2021 spreading across victims, noting the level of modifications made to the supposed antivirus as likely evidence that “the operator has access to the source code of the Sarwent malware.”
“The campaign targets people who might be concerned that they are targeted by the Pegasus spyware,” the researchers said. “This targeting raises issues of possible state involvement, but there is insufficient information […] to make any determination on which state or nation. It is possible that this is simply a financially motivated actor looking to leverage headlines to gain new access.”


Pingback: Customer Service Desk: An Easy Access For Hackers To Exploit Your Organization - SLYTECH