Three WordPress plugins have been discovered to be affected with a security shortcoming which gives a malicious actor the opportunity to take over vulnerable websites.
An attacker could update arbitrary site options on a vulnerable site, provided they could trick a site administrator into clicking a link or doing a thing.
Tracked as CVE-2022-0215, the cross-site request forgery (CSRF) flaw with a rating of 8.8 on the CVSS scale and impacting three plugins maintained by Xootix —
Login/Signup Popup (Inline Form + Woocommerce),
Side Cart Woocommerce (Ajax), and
Waitlist Woocommerce (Back in stock notifier)
CSRF occurs when an authenticated end-user is tricked by an attacker into submitting specially crafted web request. Where the victim is an admin account, CSRF can compromise the entire web application.
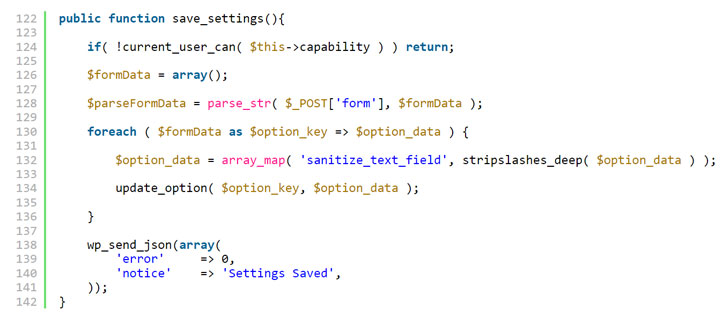
This vulnerability originates from a lack of validation when processing AJAX requests, thus effectively enabling an attacker to update the “users_can_register” (i.e., anyone can register) option on a site to true and set the “default_role” setting (i.e., the default role of users who register at the blog) to administrator, granting complete control.
Login/Signup is installed on over 20,000 sites, Woocommerece and Waitlist Wocommerce have been installed on more than 4,000 and 60,000 sites respectively.
After a disclosure by Wordfence researchers in Novem ber 2021, the issue has been addressed in Login/Signup Popup version 2.3, Side Cart Woocommerce version 2.1, and Waitlist Woocommerce version 2.5.2.
This findings come a month after attackers exploited weaknesses in four plugins and 15 Epsilon Framework themes to target 1.6 million WordPress sites as part of a large-scale attack campaign originating from 16,000 IP addresses.
Chloe Chamberland of Wordfence stated that “Though this Cross-Site Request Forgery (CSRF) vulnerability is less likely to be exploited due to the fact that it requires administrator interaction, it can have a significant impact to a successfully exploited site and, as such, it serves as an incredibly important reminder to remain aware when clicking on links or attachments and to ensure that you are regularly keeping your plugins and themes up to date.”