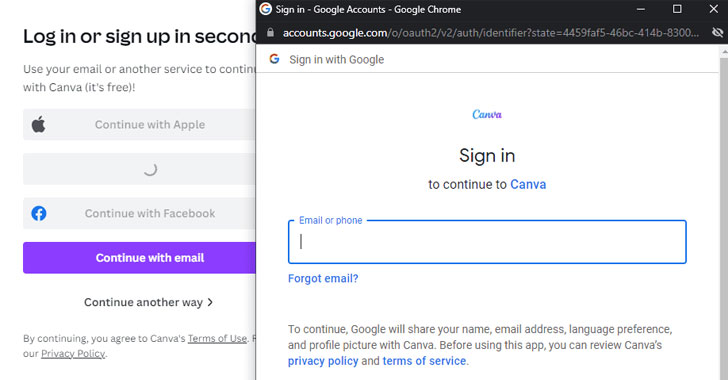
New phishing technique called browser-in-the-browser (BitB) attack can be xploited to act like a browser window within the browser in order to spoof a legitimate domain, which makes it possible to stage convincing phishing attacks. The method makes use of the third-party single sign-on (SSO) options embedded on websites such as “Sign in with Google” (of Facebook, Apple, or Microsoft).
The usual behavior when a user attempts to sign in via these methods is to be greeted by a pop-up window to complete the authentication process, the BitB attack tries to replicate this entire process using a mix of HTML and CSS code to create an entirely fabricated browser window.
“Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it’s basically indistinguishable,” mrd0x a cyber security researcher stated in a technical write-up published last week. “JavaScript can be easily used to make the window appear on a link or button click, on the page loading etc.”
This technique has been abused at least once before in February 2020, Zscaler disclosed details of a campaign that leveraged the BitB trick to siphon credentials for video game digital distribution service Steam by means of fake Counter-Strike: Global Offensive (CS: GO) websites.
“Normally, the measures taken by a user to detect a phishing site include checking to see if the URL is legitimate, whether the website is using HTTPS, and whether there is any kind of homograph in the domain, among others,” Zscaler researcher Prakhar Shrotriya said at the time.
“In this case, everything looks fine as the domain is steamcommunity[.]com, which is legitimate and is using HTTPS. But when we try to drag this prompt from the currently used window, it disappears beyond the edge of the window as it is not a legitimate browser pop-up and is created using HTML in the current window.”
Although this method significantly makes it easier to mount effective social engineering campaigns, it’s worth noting that potential victims need to be redirected to a phishing domain that can display such a fake authentication window for credential harvesting.
“But once landed on the attacker-owned website, the user will be at ease as they type their credentials away on what appears to be the legitimate website (because the trustworthy URL says so),” mrd0x added.