The criminal underworld is promoting a new phishing-as-a-service (PhaaS) toolkit called EvilProxy as a way for threat actors to get beyond the two-factor authentication (2FA) safeguards put in place against internet services.
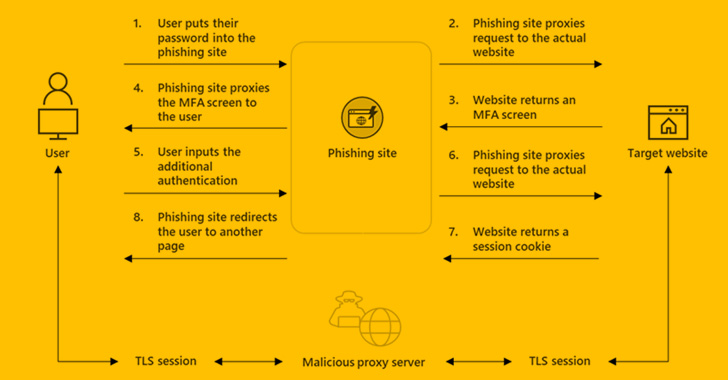
In a report published on Monday, Resecurity researchers stated that “EvilProxy actors are exploiting reverse proxy and cookie injection methods to overcome 2FA authentication – proxifying victim’s session.”
The software creates phishing links, which are merely cloned pages intended to hijack user accounts with a variety of services, including Apple iCloud, Facebook, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and Yandex, among others.
Similar to adversary-in-the-middle (AiTM) attacks, EvilProxy involves users interacting with a malicious proxy server that serves as a go-between for the target website and secretly gathers the login information, including 2FA passcodes.
It is available via subscription for a period of 10, 20, or 31 days, with the kit costing $400 per month and being accessed via the TOR anonymity network after the payment is manually made with a Telegram operator. In comparison, attacks on Google accounts can cost up to $600 per month.
According to Resecurity, “after activation, the operator will be prompted to submit SSH credentials to further deploy a Docker container and a set of scripts.” The company added that the method is similar to one used by Frappo, a PhaaS service that was made public earlier this year.
It goes without saying that the service provides a “cost-effective and scalable method” to conduct social engineering assaults, even though the selling of EvilProxy to potential customers is subject to vetting by the actors.
The revelation is just another sign that attackers are modernizing their attack toolkit to plan intricate phishing campaigns that target users in a way that can get through current security measures.
The fact that public-facing code and package repositories like GitHub, NPM, PyPI, and RubyGems are being targeted raises further suspicions that the attackers may be using these operations to facilitate supply chain attacks.
Threat actors can greatly increase the impact of campaigns by gaining unauthorized access to accounts and introducing harmful code into widely used projects created by reputable developers.
The actors very likely intend to target software developers and IT experts in order to acquire access to their repositories in order to hack “downstream” targets, according to the researchers.