Transparent Tribe, an advanced persistent threat (APT) actor based in Pakistan, pretended to be an Indian government organization in order deliver the Poseidon Linux backdoor.
Tejaswini Sandapolla, a security researcher at Uptycs, stated that “Poseidon is a second-stage payload malware connected to Transparent Tribe.” in an expert study released last week.
It is a general-purpose backdoor that gives attackers a variety of tools to take control of an infected host.
Its features include keystroke recording, screen grabs, file uploads and downloads, and different forms of remote system administration.
Transparent Tribe has a history of attacking Indian government organizations, military personnel, defense contractors, and educational institutions. It is also known as APT36, Operation C-Major, PROJECTM, and Mythic Leopard.
It has also frequently used trojanized versions of Kavach, the 2FA software that the Indian government requires, to spread a range of viruses including CrimsonRAT and LimePad to gather important data.
Late last year, another phishing attempt was discovered that used weaponized attachments to download malware intended to steal database files produced by the Kavach app.
The most recent attacks target Linux users working for Indian government organizations using a backdoored version of Kavach, showing attempts by the threat actor to broaden the scope of its attack beyond Windows and Android ecosystems.
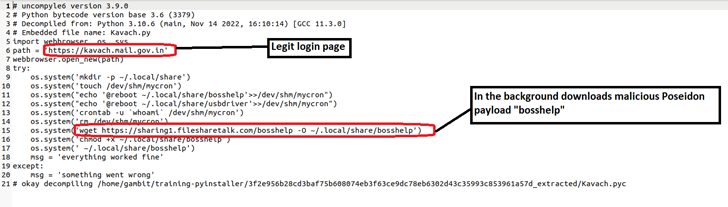
The real login page is shown to users who interact with the fraudulent Kavach in order to divert their attention, according to Sandapolla. The user’s system is compromised while the payload is downloading in the background.
The infestations are initiated by an ELF malware sample, a Python program created to collect the second-stage Poseidon payload from a remote server.
The cybersecurity firm discovered that the primary channel for the distribution of fake Kavach apps is through pirate websites that pass for legitimate Indian government websites. Websites like www.ksboard[.]in and www.rodra[.]in are among them. Users who work for the Indian government are advised to double-check any URLs they get in emails before clicking on them because Transparent Tribe’s main form of attack is social engineering.
The consequences of the APT36 attack, according to Sandapolla, “could be severe, resulting in loss of sensitive information, compromised systems, financial losses, and reputational damage.”