Since 2022, there have been over 620,000 downloads of Fleckpe, a new Android subscription virus, from the Google Play Store.
According to Kaspersky, which discovered 11 apps on the official app storefront, the virus was portrayed as authentic picture editing, camera, and smartphone wallpaper packs. The apps have since been taken down.
Although the Russian cybersecurity company’s telemetry data showed victims in Singapore, Malaysia, Indonesia, and Poland, the operation primarily targets customers in Thailand. To further avoid raising suspicion, the apps provide the stated capabilities while hiding their true intent.
The following is a list of the infringing applications:
- Beauty Camera Plus (com.beauty.camera.plus.photoeditor)
- Beauty Photo Camera (com.apps.camera.photos)
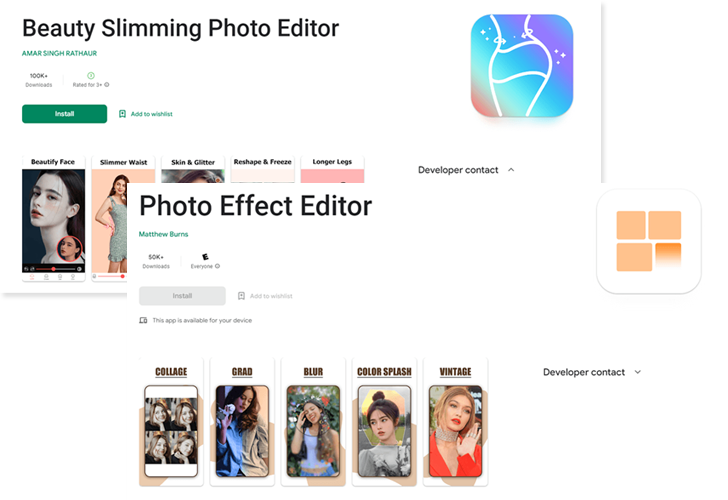
- Beauty Slimming Photo Editor (com.beauty.slimming.pro)
- Fingertip Graffiti (com.draw.graffiti)
- GIF Camera Editor (com.gif.camera.editor)
- HD 4K Wallpaper (com.hd.h4ks.wallpaper)
- Impressionism Pro Camera (com.impressionism.prozs.app)
- Microclip Video Editor (com.microclip.vodeoeditor)
- Night Mode Camera Pro (com.urox.opixe.nightcamreapro)
- Photo Camera Editor (com.toolbox.photoeditor)
- Photo Effect Editor (com.picture.pictureframe)
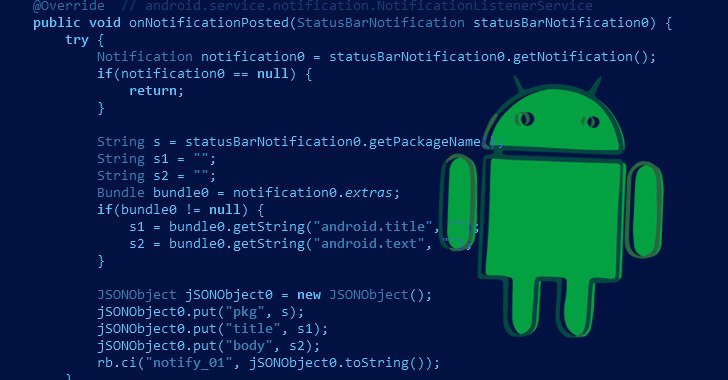
According to Kaspersky researcher Dmitry Kalinin, “the app loads a heavily obfuscated native library containing a malicious dropper that decrypts and runs a payload from the app assets” when the program first launches.
The payload, on the other hand, is designed to connect to a remote server and communicate information about the compromised device (such the mobile network code and country code for mobile phones), to which the server responds with a subscription-based web page.
The infection then loads the page in a hidden web browser window, attempts to subscribe on the user’s behalf using that window’s unauthorized access to notifications, and steals the confirmation code required to complete the process.
In order to prevent detection by security tools, recent versions of the virus have moved the majority of the hazardous functionality to the native library, showing that Fleckpe is still actively being developed.
According to Kalinin, the payload is now limited to viewing websites and intercepting notifications, serving as a link between native code and the Android components needed to make a subscription purchase.
The most recent version of the payload features some code obfuscation, but compared to the native library, it has essentially no evasion capabilities. Subscription spyware has already been discovered in the Google Play Store.
Along with Harly and Joker, Fleckpe is a member of the fleeceware family, which utilizes infected devices to subscribe to unauthorized premium services and commit billing fraud.
These apps can nevertheless be used to collect illegal fees, be repurposed by their operators to acquire a variety of sensitive information, and act as entry points for more criminal malware, despite the fact that they are not as hazardous as spyware or banking trojans.
The results, if anything, provide as additional evidence that threat actors are looking for innovative ways to distribute their programs through reliable app stores in order to scale their campaigns, mandating caution on the part of users when downloading apps and granting them permissions.
According to Kalinin, the trojans’ growing sophistication has allowed them to successfully evade the various anti-malware safeguards set up by the markets, staying unreported for protracted periods of time.