New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security
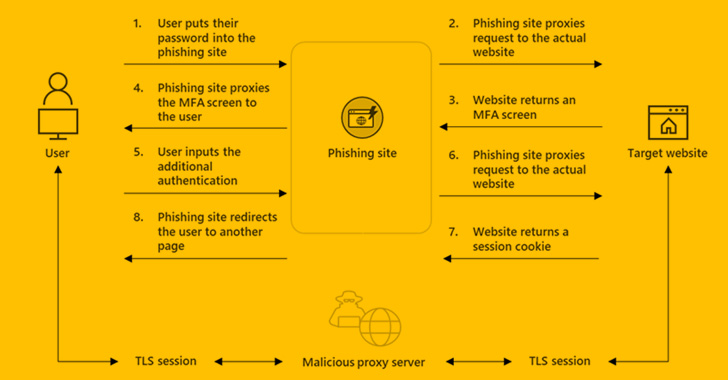
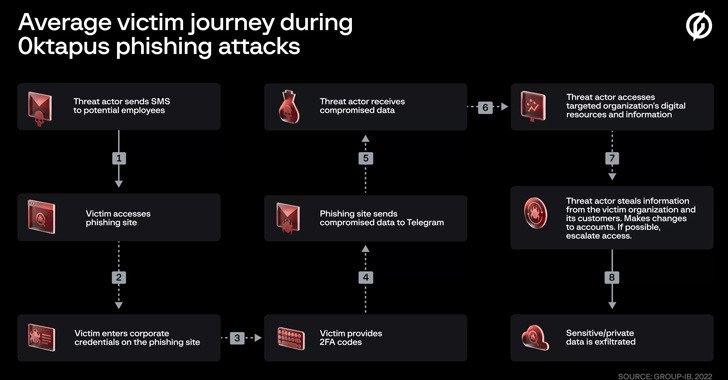
The criminal underworld is promoting a new phishing-as-a-service (PhaaS) toolkit called EvilProxy as a way for threat actors to get beyond the two-factor authentication (2FA) safeguards put in place against internet services. In a report published on Monday, Resecurity researchers stated that “EvilProxy actors are exploiting reverse proxy and cookie injection methods to overcome 2FA […]
New EvilProxy Phishing Service Allowing Cybercriminals to Bypass 2-Factor Security Read More »