Dropbox Gets Hacked
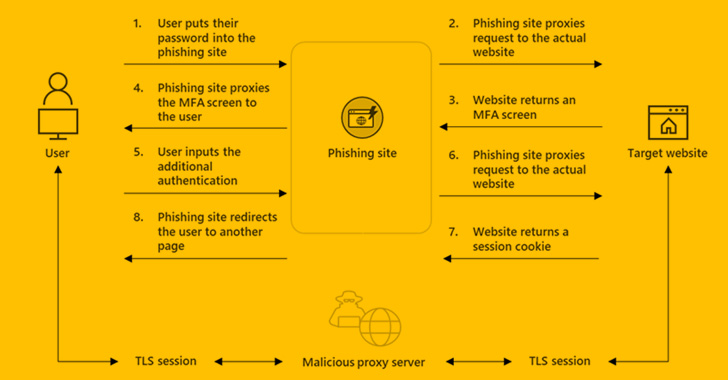
File hosting service Dropbox on Tuesday disclosed that it was the victim of a phishing campaign that allowed unidentified threat actors to gain unauthorized access to 130 of its source code repositories on GitHub. “These repositories included our own copies of third-party libraries slightly modified for use by Dropbox, internal prototypes, and some tools and […]
Dropbox Gets Hacked Read More »