New PseudoManuscrypt Malware Currently Infecting Computers
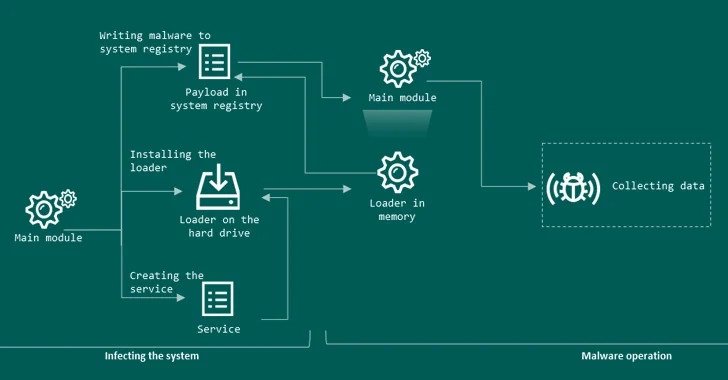
A new malware called PseudoManyscrypt has been observed attacking industrial and government organizations including enterprises in the military-industrial complex and research laboratories. The name is derived from its similarities to the Manuscrypt malware which is part of trhe Lazarus APT groups attack toolset and the series of intrusion was first detected in June 2021. It […]
New PseudoManuscrypt Malware Currently Infecting Computers Read More »