The Browser-in-the-Browser (BITB) Attack Enabling Easier Phishing Attack
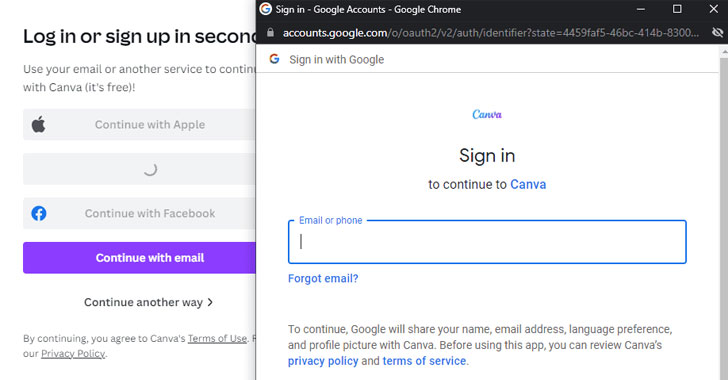
New phishing technique called browser-in-the-browser (BitB) attack can be xploited to act like a browser window within the browser in order to spoof a legitimate domain, which makes it possible to stage convincing phishing attacks. The method makes use of the third-party single sign-on (SSO) options embedded on websites such as “Sign in with Google” […]
The Browser-in-the-Browser (BITB) Attack Enabling Easier Phishing Attack Read More »